Azure Bastion let you connect via RDP and SSH to any VM in Microsoft Azure using the private IP addresses and avoiding any public exposure.
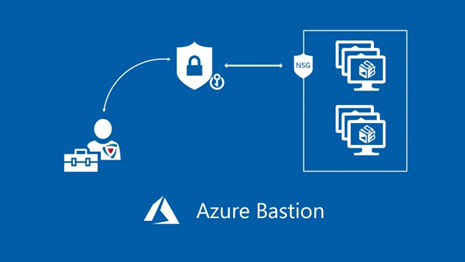
You can find many blog posts in interne and to install bastion, you can follow these the simple steps in the article below:
Azure Bastion has these main requirements:
- You must have a VNet
- In the VNet you must have a subnet named AzureBastionSubnet
- No route tables or delegations in the Bastion subnet
- You must use a subnet of at least /27 CIDR.
The only main restriction I see is the using of a subnet with a specific name because, in a complex and well-organized network scenario, all the address spaces are cataloged and organized, and the creation of a new subnet may require some changes on it.
The using of a new VNet and peering is not an applicable option because the VNet hosting the VM requires a subnet named AzureBastionSubnet anyway.
After some tests, below the applicable options.
New VNet
Of course, this is the more straightforward and the fastest. All articles mention that you create a new VNet with a subnet AzureBastionSubnet and you install your VMs in that VNet + Azure Bastion.
This method is easy, and it is a good option in case of a new VNet, but there is an important aspect to consider here, Azure Bastion requires a /27 subnet, which is an important amount of IP addresses (32).
I don’t really like the idea of using 32 IPs for that, especially because it can be reserved for many other critical scopes, but if you have small, medium company this is very applicable.
Creation of a new subnet in an existing VNet
I don’t like this idea but you can actually do that using this option, and I will explain to you why I don’t like it. You can change the address space of your VNet and add more space in your network, after that you can add the new subnet named AzureBastionSubnet.
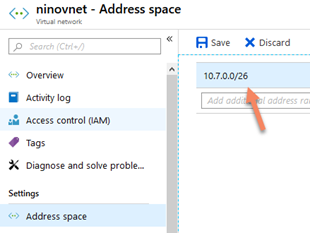
As I mentioned before, this is not easily applicable in a well-organized network infrastructure because the addresses spaces have been already assigned to regions and departments and this method will require an important effort for the network team.
If you don’t have this problem, then I would say that maybe you still need to organize your network strategy and I would recommend you to do that asap.
Dedicate an address space to Azure Bastion
This is, in my opinion, the best option for using Azure Bastion.
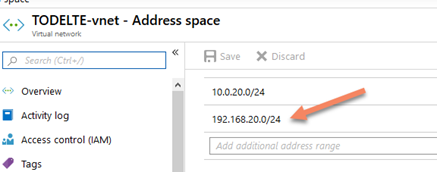
We dedicate a specific IP schema for Azure Bastion, for example, the 192.168.*.*, and we use these IP schemas for that only.
As you can see below, you can add the new addresses space to you VNet
And you can create the AzureBastionSubnet subnet
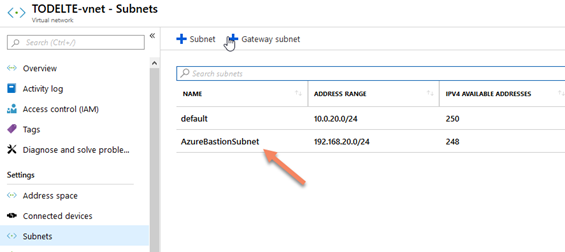
This is the best way to use Azure Bastion because you dedicate a specific IP range to that and you touch your network design at all.

