In my last sessions and studies, I shared a lot of techniques to attack containers. The most effective is the reverse shell.
Microsoft is pushing a lot on the defence side for containers, below a very useful point of reference.
https://docs.microsoft.com/en-us/azure/defender-for-cloud/defender-for-containers-introduction?tabs=defender-for-container-arch-aks
In my last session, I show how criminals usually operate below the process.
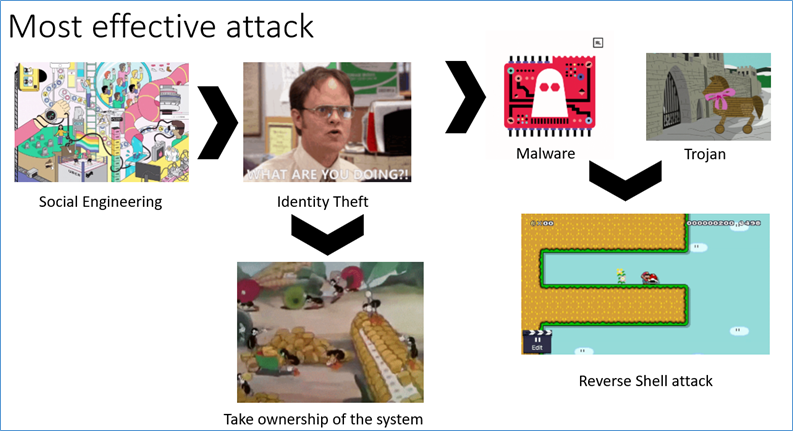
Social engineering is always the most effective technique, and the criminal steals the identity, which drives him in two ways.
- He uses this identity to obtain the credentials and slowly take ownership of the systems.
- He uses this identity to send malware or trojan containing the attack, in the case of a container, a reverse shell attack.
The reverse shell attack is very common due to how firewalls are usually configured on servers: a firewall will rarely allow direct access to a shell from an unknown address, and the only ports widely open to the entire network will most likely be port 80 (HTTP) and 443 (HTTPS). Unlike incoming ports, firewalls do not usually limit outgoing connections from the server, and this could allow an attacker to establish a connection between one of his servers (preferably with a public IP from which it is possible to do routing if the goal is a remote machine) and the machine targeted by the use of tools such as netcat, starting the connection from the remote machine (removing the restrictions of the incoming rules imposed by the firewall) and simply waiting for that connection.
Below is a nice video from Null Byte
https://www.youtube.com/watch?v=VF4In6rIPGc
Microsoft now renamed and unified several security stacks like Security Center and Microsoft Defender in Microsoft Defender for Cloud.
More insights are below:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/release-notes#recommendations-to-enable-microsoft-defender-plans-on-workspaces-in-preview
An interesting feature in the preview is the Microsoft Defender plans, now in preview.
A very interesting article is the original announcement from Microsoft. I recommend this reading.

