Threat hunting is a proactive cybersecurity practice that involves searching through networks, systems, and datasets to detect and isolate advanced threats that evade existing security solutions. With the increasing adoption of cloud services, Microsoft Azure has become a focal point for threat hunters looking to safeguard their organization’s cloud infrastructure. This article outlines a comprehensive approach to threat hunting in Microsoft Azure, focusing on strategies, tools, and best practices to identify and mitigate potential security threats.
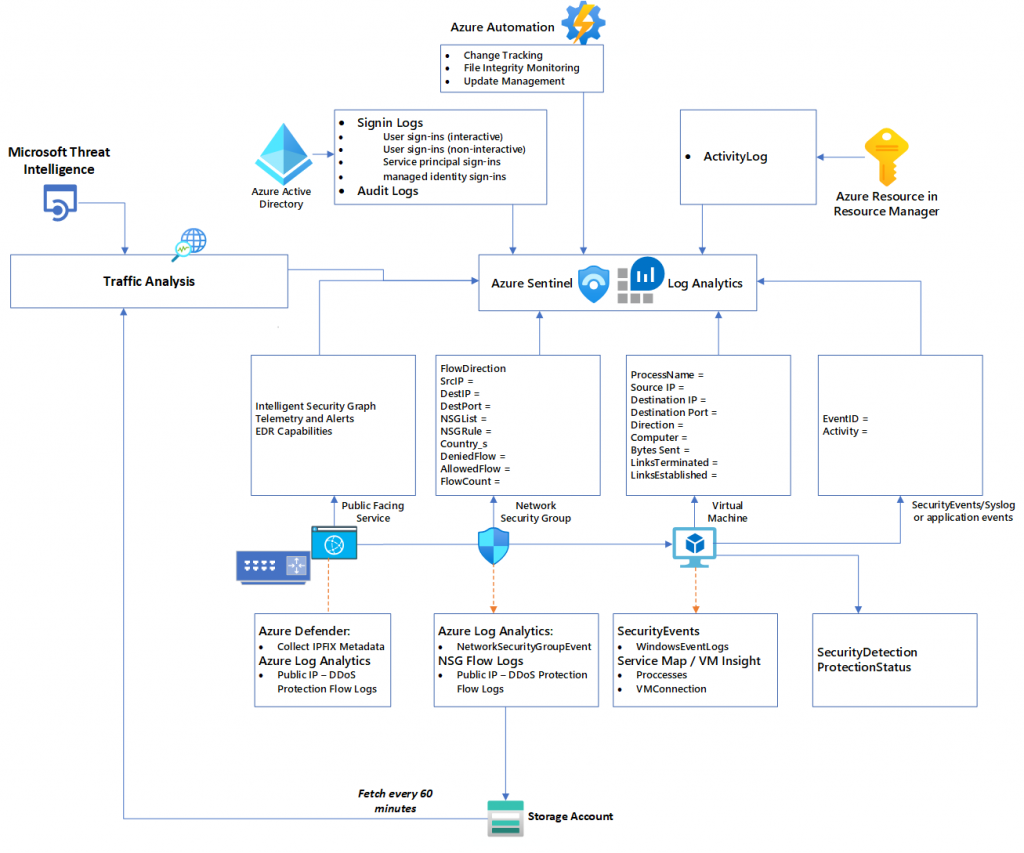
Understanding the Azure Environment
Before diving into threat hunting, it’s crucial to have a deep understanding of the Azure environment and its components. Azure offers a wide range of services, including Virtual Machines, App Services, Azure Active Directory, and more. Familiarize yourself with the architecture, network configurations, and security controls in place. This knowledge is foundational for effectively monitoring and analyzing the environment for potential threats.
Setting Up for Threat Hunting
Enable Logging and Monitoring
Azure provides various tools for logging and monitoring that are essential for threat hunting:
- Azure Monitor: Collects, analyzes, and acts on telemetry data from Azure and on-premises environments.
- Azure Security Center: Offers advanced threat protection and security health monitoring across Azure resources.
- Azure Sentinel: A scalable, cloud-native SIEM and SOAR solution.
Ensure that logging is enabled for all relevant resources and that you have access to these tools for analysis.
Azure Monitor
Azure Monitor is a powerful service that collects, analyzes, and acts on telemetry data from both Azure and on-premises environments. It plays a critical role in threat hunting by providing the visibility needed to understand what’s happening across your applications, infrastructure, and network.
- Data Collection: Azure Monitor can collect data at various levels, including application monitoring, guest OS monitoring, Azure resource monitoring, and subscription-level monitoring. This data encompasses metrics, logs, and traces that are essential for detecting anomalies.
- Analysis Tools: It provides a range of analysis tools such as log queries and metrics analysis to help dissect the collected data. These tools are instrumental in identifying patterns or anomalies that could indicate a security threat.
- Alerting: Azure Monitor allows you to create alert rules based on specific metrics or query results. These alerts can trigger notifications or automated actions, enabling quick responses to potential security incidents.
- Integration: The service integrates with other Azure services like Azure Logic Apps, providing the ability to automate workflows in response to monitoring data. This integration is vital for orchestrating swift and efficient threat mitigation strategies.
Azure Security Center
Azure Security Center offers advanced threat protection and security health monitoring across Azure resources. It serves as a unified infrastructure security management system that strengthens the security posture of your data centers.
- Continuous Assessment: Azure Security Center continuously assesses your Azure resources for security issues and provides recommendations to improve your security posture. This proactive assessment helps in identifying potential vulnerabilities before they can be exploited.
- Advanced Threat Protection: It utilizes advanced analytics and global threat intelligence to detect and mitigate threats. By analyzing signals across Azure, it can identify patterns that indicate a breach or an ongoing attack.
- Just-In-Time Access: One of its notable features is the Just-In-Time (JIT) VM access, which reduces exposure to attacks by enabling you to lock down inbound traffic to your VMs, opening access only when needed and for a limited time.
- Regulatory Compliance: Azure Security Center also helps in maintaining regulatory compliance by providing insights into your compliance posture with respect to industry standards and regulations. This feature aids in ensuring that the environment aligns with best practices and legal requirements.
Azure Sentinel
Azure Sentinel stands out as a scalable, cloud-native Security Information and Event Management (SIEM) and Security Orchestration Automated Response (SOAR) solution. It provides intelligent security analytics and threat intelligence across the enterprise, making it faster to detect, investigate, and respond to threats.
- Data Aggregation: Sentinel aggregates data from all sources, including users, applications, servers, and devices running on-premises or in any cloud, providing a comprehensive view of your entire network.
- AI and Threat Intelligence: Leveraging artificial intelligence and Microsoft’s vast threat intelligence, Sentinel identifies known and unknown threats, offering actionable insights to respond to incidents.
- Automated Security: With built-in SOAR capabilities, Azure Sentinel automates common tasks and orchestrates complex workflows in response to detected threats. This automation is key to reducing the workload on security teams and accelerating response times.
- Community and Templates: Azure Sentinel benefits from a growing community and marketplace, where templates for workbooks, notebooks, and playbooks can be shared and utilized, enhancing the tool’s effectiveness and enabling customized threat hunting strategies.
Leverage Azure Policies
Implement Azure policies to enforce security standards and compliance across your Azure environment. These policies can help mitigate risks by ensuring that configurations do not deviate from established security practices.
Conducting Threat Hunting
Hypothesis Generation
Threat hunting typically starts with a hypothesis based on known threats, anomalies, or indicators of compromise (IoCs). These hypotheses guide the search for malicious activity within the Azure environment.
Data Collection and Analysis
Collect data from Azure logs, network traffic, and endpoint devices. Use Azure Monitor and Sentinel to aggregate and analyze this data. Look for unusual activity that could indicate a threat, such as:
- Anomalies in login patterns
- Unexpected resource deployments
- Irregular network traffic
Anomalies in Login Patterns
Anomalies in login patterns can indicate unauthorized access attempts or compromised credentials. These anomalies might include logins at unusual times, repeated login failures, or logins from geographically improbable locations.
- Azure Active Directory (Azure AD) and Azure Monitor: Utilize Azure AD’s sign-in logs in conjunction with Azure Monitor to analyze login patterns. Azure AD provides detailed information on user sign-ins, enabling you to detect unusual activities such as multiple failed login attempts or successful logins from unexpected locations.
- Alerting and Analytics: Set up alerts for anomalous sign-in activities using Azure Monitor. By defining specific criteria for what constitutes abnormal behavior, you can receive immediate notifications and take action to investigate and mitigate potential threats.
- Azure AD Identity Protection: Leverage Azure AD Identity Protection to automatically detect and respond to potential identity-based threats. It uses machine learning and heuristics to identify irregular sign-in activities and can enforce risk-based policies to either block access or require additional authentication steps.
Unexpected Resource Deployments
Unexpected or unauthorized resource deployments can be a sign of an attacker exploiting your Azure environment to deploy resources for malicious purposes, such as crypto mining or as part of a larger attack.
- Azure Policy and Azure Security Center: Use Azure Policy to enforce organizational standards and assess compliance across your resources. Azure Security Center can detect and alert on unexpected resource deployments, providing insights into resources that may have been deployed without adherence to organizational policies.
- Activity Logs and Resource Graph: Monitor Azure Activity Logs and use Azure Resource Graph to query resources across your environment. These tools can help identify newly deployed or modified resources that don’t match typical deployment patterns or that have been deployed outside of approved deployment windows.
Irregular Network Traffic
Irregular network traffic, such as unusual outbound connections, spikes in data transfer, or unapproved protocol usage, can indicate data exfiltration, command and control (C2) communication, or other malicious activities.
- Azure Network Watcher and Azure Firewall: Utilize Azure Network Watcher’s traffic analytics and Azure Firewall’s application and network rules to monitor and control network traffic. These tools can help identify and investigate unusual traffic patterns or connections that deviate from normal baseline activity.
- Azure Sentinel: Incorporate Azure Sentinel for advanced threat detection capabilities. Sentinel can aggregate data from various sources, including network traffic, enabling complex queries and analytics to identify potentially malicious activity. Utilize pre-built or custom queries to monitor for irregular traffic patterns.
- Playbooks and Automated Responses: Create playbooks in Azure Sentinel to automate responses to detected network anomalies. For example, if an anomaly is detected, a playbook can automatically create an incident, gather related data, and initiate predefined mitigation actions.
Incorporating these strategies into your threat hunting practices allows for the proactive identification and mitigation of potential security threats within Azure. Leveraging Azure’s comprehensive tools and services enables organizations to monitor for, analyze, and respond to anomalies effectively, enhancing the overall security posture of their cloud environment.
Utilize Threat Intelligence
Incorporate threat intelligence to identify known IoCs within your Azure environment. Azure Sentinel can integrate with various threat intelligence platforms to enhance your hunting capabilities.
Investigation and Isolation
Upon detecting suspicious activity, investigate to understand the scope and impact. Use Azure’s tools to isolate affected resources and prevent further compromise.
Remediation and Strengthening
After isolating the threat, develop a remediation plan to remove the adversary from the environment. Following remediation, analyze the breach to improve security measures and prevent similar attacks.
Best Practices for Threat Hunting in Azure
- Continuous Learning: Stay updated with the latest threat intelligence and Azure security features.
- Automate Responses: Use Azure Sentinel playbooks to automate responses to common threats, reducing the time from detection to remediation.
- Collaborate: Share findings with the security community to help others and gain insights from their experiences.
- Documentation and Reporting: Document all threat hunting activities and findings for future reference and compliance requirements.
Conclusion
Threat hunting in Microsoft Azure is a critical component of a robust cybersecurity strategy. By proactively searching for threats, organizations can significantly enhance their security posture in the cloud. The key to successful threat hunting lies in a deep understanding of the Azure environment, leveraging the right tools, and continuously evolving strategies to counter emerging threats. With a proactive and informed approach, organizations can safeguard their Azure resources against sophisticated cyber threats.

