Social engineering remains one of the most significant threats to cloud security, exploiting human error rather than technical vulnerabilities. In this detailed guide, we delve into how Maltego, a renowned open-source intelligence (OSINT) and graphical link analysis tool, can be utilized for conducting comprehensive social engineering assessments on cloud solutions. This technical walkthrough aims to equip security professionals with the knowledge to identify and mitigate social engineering vectors effectively.
Understanding Maltego
Maltego is an interactive data mining tool that renders directed graphs for link analysis. It is widely used in online investigations to uncover the relationships between pieces of information from various sources on the Internet. Maltego excels in gathering and connecting information for investigative tasks and is particularly useful in the realm of social engineering assessments.
- Getting Started with Maltego: Familiarize yourself with Maltego by visiting Maltego’s official website and accessing their documentation.
Preparation Phase
- Define the Scope: Clearly outline the boundaries of your assessment, focusing on specific cloud services, infrastructure, and personnel within the organization.
- Gather Initial Data: Start with basic information about the target cloud solution, including domain names, IP addresses, and any publicly known email formats used by the organization.
- Set Up Maltego: Download and install Maltego from Maltego Downloads. Choose the edition that best suits your assessment needs.
Conducting the Assessment with Maltego
Step 1: Domain and Email Harvesting
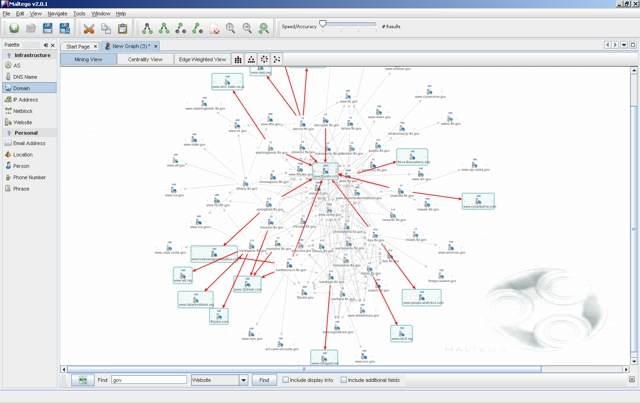
- Domain Information Gathering: Use Maltego to gather information about the cloud solution’s domain. This can involve DNS records, subdomains, and associated IP addresses. Utilize the
DNS from Domaintransform to start mapping out the target’s infrastructure. - Email Address Discovery: Maltego’s
Email Address from Domaintransform can help identify potential targets for social engineering by uncovering email addresses associated with the domain. These addresses can provide hints on the naming convention used by the organization.
Step 2: Social Network Analysis
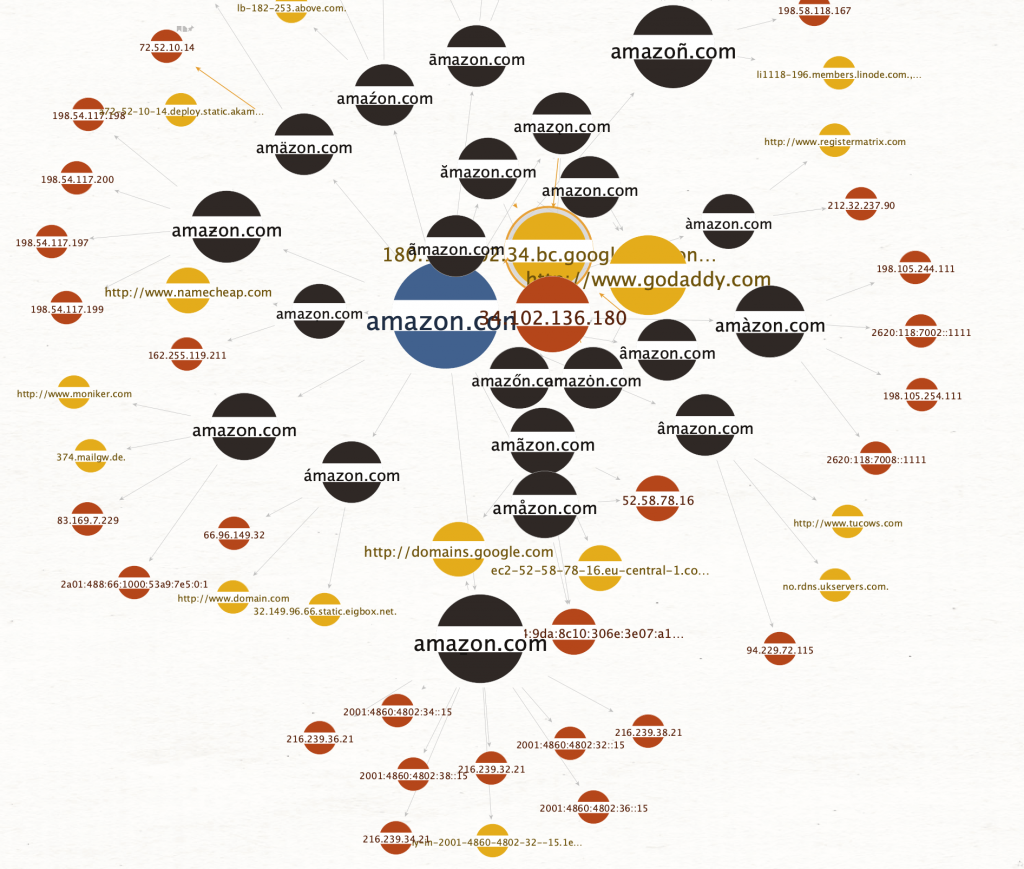
- Identify Key Individuals: Using the discovered email addresses, search for profiles on social networks. Maltego’s integrations with social media platforms can help identify employees and their roles within the organization.
- Analyze Relationships: Construct a graph of relationships between identified individuals and external entities. This analysis can reveal potential vectors for social engineering attacks, such as trusted external partners or vendors.
Step 3: Data Aggregation and Analysis
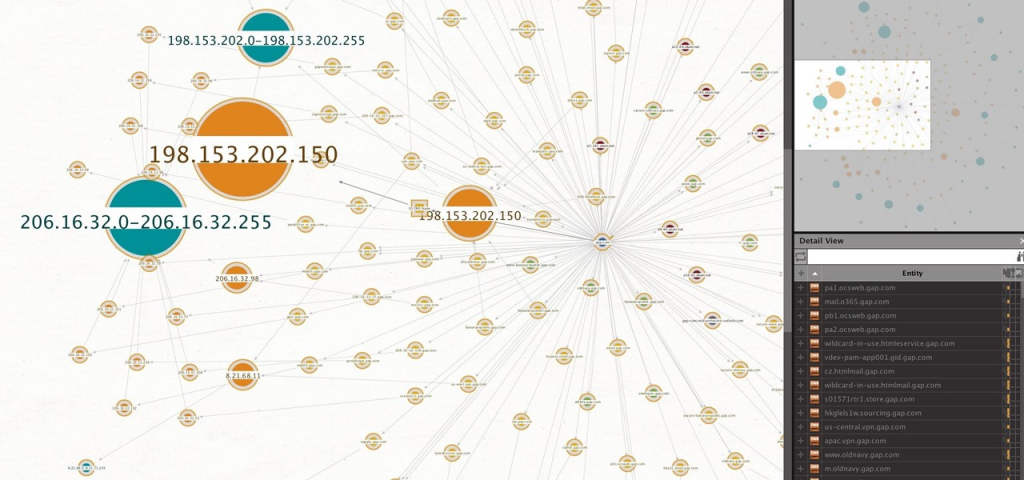
- Aggregate Data: Combine the collected data to form a comprehensive picture of the target organization’s online footprint, including any publicly shared information that could be used in crafting social engineering campaigns.
- Vulnerability Identification: Look for information that could be exploited, such as employees sharing too much work-related information on social media, weak points in the organization’s online presence, or outdated cloud software revealed through DNS records.
Mitigation and Strategy Development
- Develop Awareness Training: Based on the findings, develop targeted awareness training for employees, focusing on the specific types of social engineering attacks they are most likely to face.
- Strengthen Policy and Procedures: Recommend enhancements to policies and procedures that could reduce the risk of successful social engineering attacks. This might include stricter information sharing guidelines on social media.
- Technical Safeguards: Suggest the implementation of technical safeguards such as two-factor authentication (2FA), email filtering, and endpoint protection solutions to mitigate the risk of successful attacks.
Reporting and Follow-up
- Detailed Reporting: Create a detailed report of your findings, including the methods used, data discovered, and potential vulnerabilities identified. Offer clear recommendations for mitigating these risks.
- Follow-up Assessments: Social engineering landscapes evolve rapidly; thus, regular follow-up assessments are crucial. Schedule periodic reviews to ensure that mitigation strategies remain effective and to identify new potential threats.
Conclusion
Maltego offers a powerful suite of tools for conducting social engineering assessments, enabling security professionals to uncover and mitigate potential threats in cloud environments. By systematically gathering and analyzing information related to the target organization, you can identify vulnerabilities before they are exploited by attackers. It’s crucial to combine the insights gained from Maltego with comprehensive security awareness training and robust technical defenses to protect against the ever-present threat of social engineering.
Further Reading and Resources
- Maltego Documentation: Comprehensive guide and tutorials available at Maltego Docs.
- Social Engineering Best Practices: For in-depth strategies on combating social engineering, visit SANS Social Engineering Whitepapers.
- Cloud Security Alliance: Access a wealth of resources on cloud security best practices at Cloud Security Alliance.
By staying informed and vigilant, organizations can significantly reduce the risk posed by social engineering to their cloud solutions.

