This is a guideline to manage the Cyber Security and threats in Azure, I will keep this guideline updated.
Introduction
We have many ways to manage and handle threats and security, Microsoft Azure offers any type of tool and technology, starting from the classical line of defences like firewall, encryption, network security group, MOMS, Security Centre, Audit Logging, GDPR and much more.
We first need to identify the most important risks and threats and how to face and manage them, but we also need to choose the best platform able to provide us with the best features and tools.
GDPR
A comparison with the other offering cloud companies, Amazon and Google, Microsoft is in my opinion the most valuable offer in term of costs and value back.
Microsoft is conducting very important investments around Cyber Security, actually it is the only one company able to offer a complete suite to manage the General Data Protection Regulation, the Compliance Manager, the difference between Compliance Manager and the other offers are important, GDPR is a key topic.
Essentially, Microsoft shared the same platform they use to manage the GDPR internally, the platform drives the user on better understanding the requirements, the risks and it provides the solutions and best practices as well.
Amazon offers an extensive landscape of documentation, “blog articles” and support, but this is not something that a user is able to handle by himself, we need to involve a lot of support and we need a deep legal knowledge in order to understand what we are reading about, even if we are legal.
The Google Cloud offer is similar to AWS, a bit better articulated in my opinion but it is still document and support based
Threats and tools
We also need to plan our risk assessment in relation with the overall trend, we need references and we need updated information, the threats techniques evolution is proportional with the technology evolution, at the same speed.
Verizon provides the annual breach trends report we need to use this report to better understand where the most common threats are and where they come from, this is useful to identify the critical areas in the company and in our cloud infrastructure.
Looking at the actual report, the 75% of the breaches are perpetrated by an outsider, so that naturally means a firewall, but in the other hand the 81% of most tactic used to achieve that is perpetrated by stolen and/or weak password.
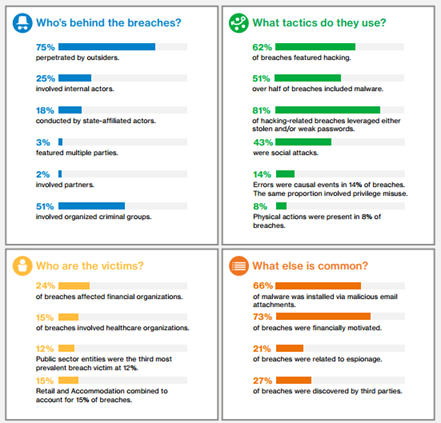
So, this is not just a matter of technology to use but also an internal methodology to use and able to educate the employees on a better way to protect the data and the company.
To identify the most common threats and the current trend we need to refer to the ENISA Threat Landscape Report , you can find 2016 here, this is the bible of the security threats.
Looking at the 2016 report the most common threat is Malware so antivirus, Web based and application attacks is the second, so DMZ and denial of service fourth.
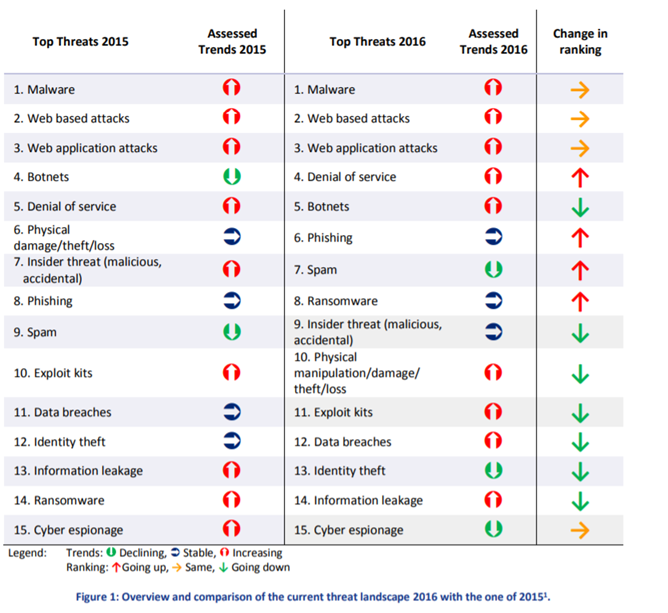
Very interesting is the increment of Ransomware, a software crypt your data or block your system unless a ransom is paid, but the software needs to be installed, so who installed the software, and how?, in this case, again, it is a matter of educating the employees and the company.
We need to check which application or software is more exposed to the threats, I recommend the website Information is Beautiful , this site gathers all the information and it provides very useful graphs able to provide very important information.

