Ensuring the security of your Azure Landing Zone (ALZ) is paramount in the current cyber threat landscape. Azure Landing Zones provide a structured approach for setting up your Azure environment, emphasizing scalability, security, and governance. This article offers a detailed, technical guide on leveraging Shodan and the Metasploit Framework to comprehensively scan and assess vulnerabilities within an ALZ, enriched with links to further your understanding and implementation.
Understanding the Tools
- Shodan is a specialized search engine for finding internet-connected devices, offering insights into publicly exposed assets, open ports, and potential vulnerabilities. It’s an invaluable tool for identifying risks in Azure environments. Discover more about Shodan’s capabilities at Shodan.io.
- Metasploit Framework is an open-source project for security research and penetration testing. It facilitates the development and execution of exploit code against remote target machines, aiding in vulnerability discovery and mitigation. Learn about the Metasploit Framework at Metasploit.com.
Step 1: Azure Landing Zone Preparation
Proper preparation involves a thorough inventory and understanding of your ALZ’s assets and architecture. Microsoft offers comprehensive guidance on setting up and managing Azure Landing Zones, available at Azure Landing Zones documentation.
Step 2: Shodan Scans
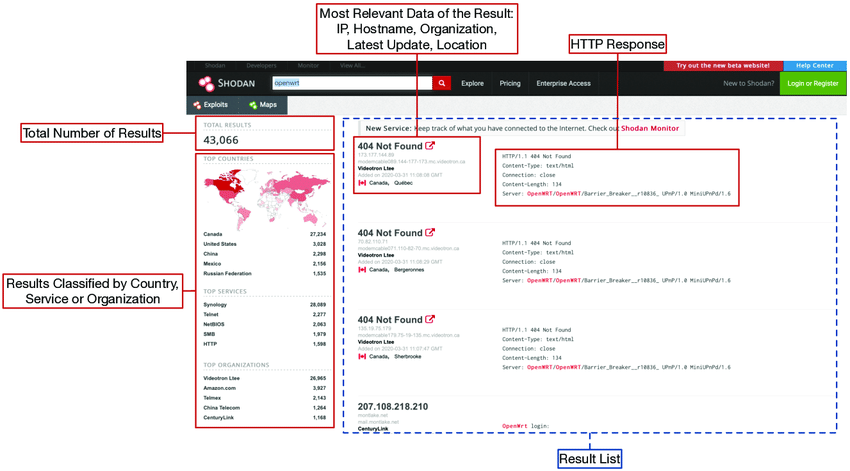
- Identifying Targets: Utilize Shodan to pinpoint exposed resources within your ALZ. Effective searches can be conducted using IP ranges or Azure-specific query filters. Shodan provides a guide on constructing effective searches at Shodan Search Guide.
- Analyzing Findings: Shodan’s output can reveal critical information about your assets. Prioritize findings based on potential exposure and vulnerability. Shodan’s documentation, available at Shodan Documentation, offers insights into interpreting search results.
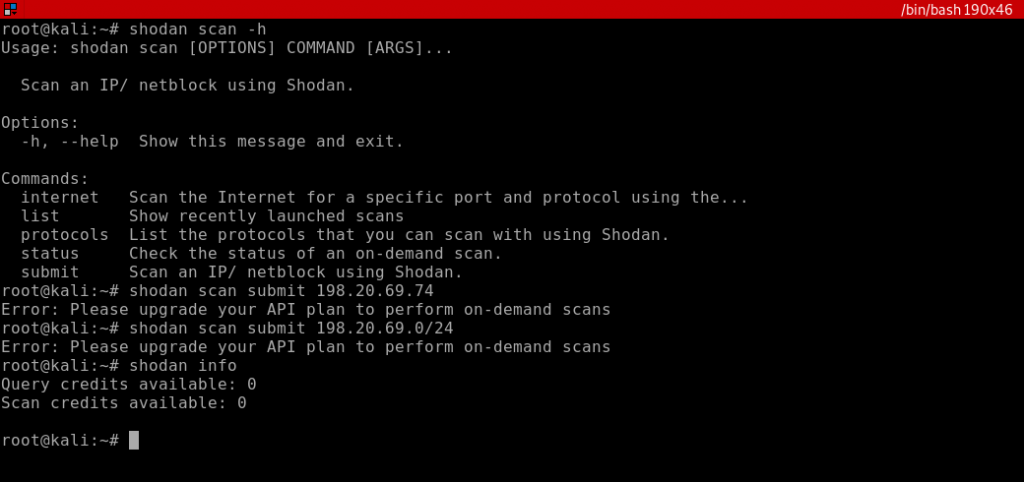
- Practical Tip: Automate and refine your scans with Shodan’s CLI, which is documented extensively at Shodan CLI Documentation.
Step 3: Metasploit Vulnerability Assessment
- Setup: Installation guides for the Metasploit Framework are available at Metasploit Installation Guide, catering to various operating systems.
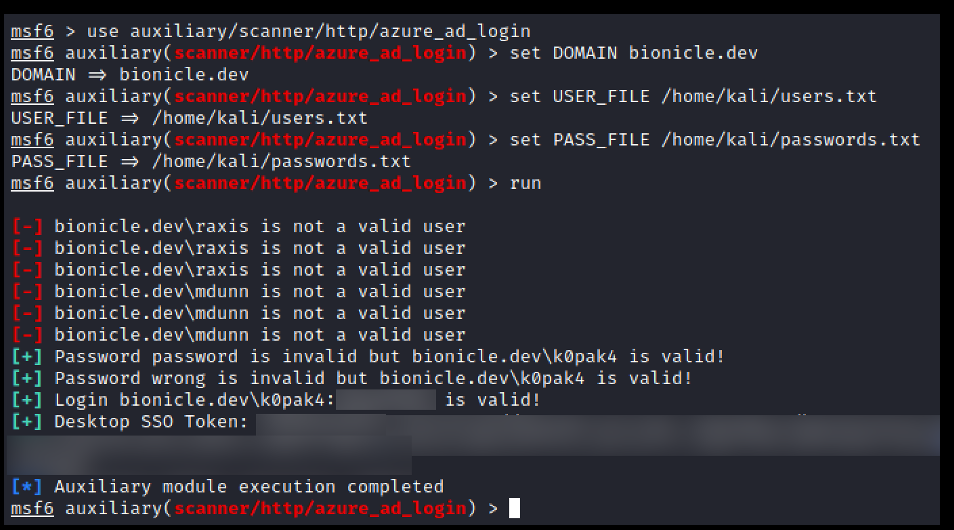
- Selecting Modules: Choose appropriate modules based on preliminary Shodan findings. Metasploit’s vast module library is documented at Metasploit Modules, where you can find specific exploits or scanners tailored to identified vulnerabilities.
- Executing Tests: Conduct your assessments with Metasploit, ensuring you have authorized access to target assets. Rapid7 provides a comprehensive guide on using Metasploit at Metasploit Unleashed.
- Analyzing Results: Post-assessment, evaluate the findings for actionable intelligence. Remediation strategies should be prioritized based on the severity and impact of the discovered vulnerabilities.
Step 4: Remediation and Reporting
Address identified vulnerabilities with urgency, applying best practices for patching, configuration adjustments, and security enhancements. Documenting your findings and actions is crucial for compliance and future assessments. Microsoft Azure provides tools and guidelines for security best practices and remediation strategies at Azure Security Documentation.
Best Practices and Considerations
- Ensure compliance with legal and regulatory mandates before initiating scans or penetration tests. Guidance on ethical and legal penetration testing can be found at Ethical Hacking Guidelines.
- Integrate vulnerability assessment into your continuous monitoring strategy to detect and mitigate threats proactively. Azure offers solutions for continuous monitoring, detailed at Azure Monitor.
- Leverage Azure’s native security features, such as Azure Security Center, to bolster your security posture. Explore these features at Azure Security Center.
Conclusion
Securing an Azure Landing Zone is an ongoing process that requires diligence, the right tools, and a proactive approach. By utilizing Shodan and the Metasploit Framework for scanning and vulnerability assessment, you can uncover and address potential security issues, enhancing your ALZ’s defense mechanisms. Stay informed and utilize the wealth of resources available to ensure your Azure environment remains robust against evolving cybersecurity threats.

