In an era where data forms the lifeblood of businesses, understanding the importance of Cloud Architecture and its associated security measures has become paramount. As we delve into this topic, we encounter a concept often overlooked by many cloud architects – the CIA triad.
The CIA triad, an acronym for Confidentiality, Integrity, and Availability, is a fundamental security model that forms the foundation for any organization’s data security policy. These principles are often seen as the pillars of information security and are crucial in maintaining a well-secured cloud environment.
In this article, we aim to discuss how cloud architecture often falls short of incorporating these vital principles and how the resultant architecture can vary starkly from one that is rooted in the CIA triad. We will walk you through the process of designing a generic cloud architecture for integration, then revisit it with the CIA triad in mind, revealing a profound transformation in the architecture’s robustness and resilience.
No matter what your level of technical expertise, this article will strive to present this complex topic in an accessible and easy-to-understand manner, so that everyone can grasp the significance of the CIA triad in the context of cloud architecture.
Cloud computing has revolutionized the way businesses operate and innovate. From storing vast quantities of data to running complex applications, cloud platforms have emerged as an integral part of a company’s digital infrastructure.
But with this increased dependency comes a heightened risk to data security and deliver what I call a spaghetti architecture.
When we say “data,” we don’t simply mean the traditional conception of binary 1s and 0s stored in databases, or the entries in an Excel spreadsheet. We’re talking about a holistic view of data as an entity that forms the basis of all digital operations, interconnections, and ultimately, the value creation in today’s enterprises.
Everything that is processed, stored, or transferred in the digital realm can be considered data. This extends to every file, every line of code, every message exchanged, every application running, every virtual machine hosted, every transaction made – it all boils down to data. By acknowledging this comprehensive definition of data, we can start to understand its omnipresence in our digital environments, especially within the sphere of cloud computing.
Take, for instance, a service running on a cloud platform. While we might view it as a functional entity, at its core, it is essentially composed of data. This includes the service’s underlying code, its runtime configurations, the requests it processes, the responses it returns, and the logs it generates. All of these are various forms of data.
Similarly, a virtual machine (VM), which is essentially a software emulation of a physical computer, is fundamentally a complex amalgamation of data. The operating system, applications, and files it hosts, its configuration and state information – all of these are data. Moreover, the very operation of a VM, including its instantiation, snapshotting, migration, and termination, all involve the manipulation of vast amounts of data.
Then we have databases, the traditional custodians of data. Modern databases, especially those hosted on cloud platforms, do much more than merely storing data. They offer sophisticated mechanisms to ensure data’s availability, consistency, and durability. They provide features to query and analyze data, thereby transforming raw data into actionable insights. Again, each of these functionalities is deeply rooted in the handling of data. Even the very messaging and communication that keep the various components of a cloud architecture connected hinge on data. Every API request, every message passed through a message queue, every notification triggered – they all are data in transit.
Furthermore, consider the security and auditing mechanisms that protect and govern our digital environments. They operate by analyzing patterns in data, detecting anomalies, enforcing rules, and logging activities – all data-centric tasks.
When you grasp this all-encompassing nature of data, you understand that designing, deploying, and managing a cloud architecture is essentially about managing data. It’s about ensuring that the data, in all its forms and throughout its lifecycle, remains confidential, maintains its integrity, and is always available when needed – the principles of the CIA triad.
In essence, by understanding and acknowledging that everything in our digital ecosystems is data, we can appreciate the crucial role of the CIA triad in shaping a secure, resilient, and robust cloud architecture. It is this profound relationship between data and the CIA triad.
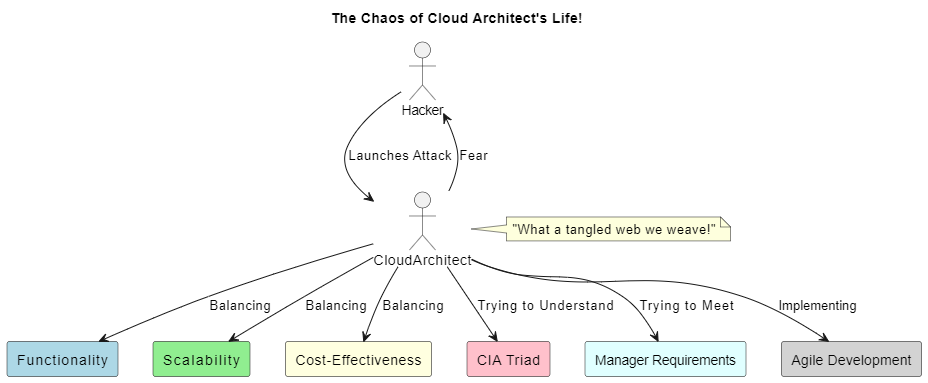
Often, cloud architects focus on the functionality, scalability, and cost-effectiveness of their designs. While these factors are undeniably crucial, an equally important aspect – security, tends to get sidetracked.
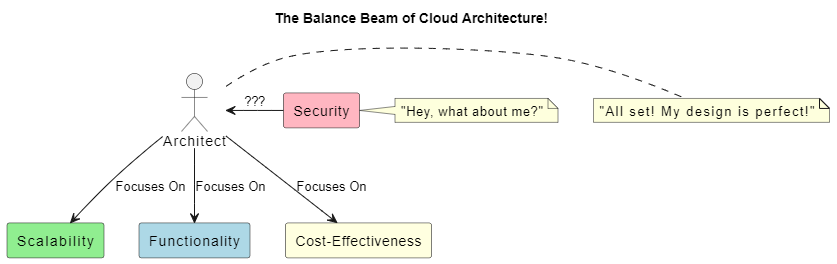
Not integrating security principles like the CIA triad from the get-go can lead to severe vulnerabilities, possibly making the cloud environment a soft target for cyber threats. Interestingly, the application of the CIA triad is not a sophisticated or cryptic task. It’s about understanding the basic principles of data security – Confidentiality, ensuring that the data is accessible only to those authorized; Integrity, assuring that the data remains unchanged and trusted throughout its lifecycle; and Availability, ensuring that the data remains accessible when needed.
By incorporating these principles into the very fabric of a cloud architecture design, we can create a more resilient and secure environment. To illustrate this, we will take you on a journey, starting with a simple cloud architecture designed for integration, showing you how it evolves when viewed through the lens of the CIA triad.
In my perspective, creating a robust, effective cloud architecture without embedding the principles of the CIA triad – Confidentiality, Integrity, and Availability – is akin to constructing a building without a solid foundation. It might stand, it might even function for a while, but sooner or later, the lack of foundational support will precipitate a collapse. In the context of cloud architecture, this “collapse” could manifest as data breaches, service disruptions, or even systemic failures – scenarios that any organization would want to prevent.
The concept of designing a cloud architecture seems daunting to many, primarily due to the complex interplay of various components and the looming threat of cyber risks. However, adopting the CIA triad can drastically simplify this task. This is because the CIA triad acts as a guiding light, a North Star that aligns all the components of the architecture towards a common goal – a secure, resilient, and reliable digital ecosystem.
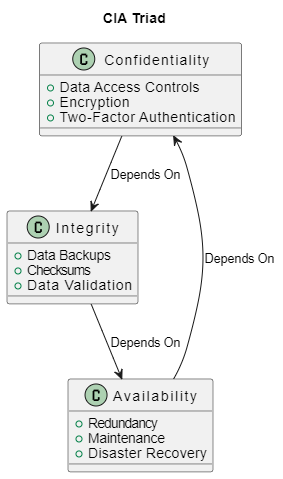
Confidentiality ensures that data, in all its forms and manifestations, is only accessible to authorized entities. This principle enforces access controls and encryption mechanisms, leading to a robust defense against unauthorized access and data leaks. Designing a cloud architecture with confidentiality in mind implies incorporating robust authentication and authorization mechanisms, securing data at rest and in transit, and enforcing least privilege access.
Integrity guarantees that the data remains unaltered during storage and transmission, ensuring it’s trustworthy and accurate. This involves implementing measures like checksums, hashing algorithms, and digital signatures that verify the data’s authenticity. In the context of a cloud architecture, integrity could mean employing reliable storage solutions, securing network communications, and implementing effective data validation mechanisms.
Availability, the third pillar of the CIA triad, emphasizes that the data and services should always be accessible when needed. This necessitates designing an architecture that is resilient to failures, can scale in response to demand, and has effective disaster recovery strategies. These considerations lead to the adoption of practices like load balancing, auto-scaling, redundancy, and regular backups.
When we view cloud architecture through the lens of the CIA triad, what earlier seemed like a jumble of services, configurations, and data flows, now organizes itself into a structured design that is driven by the principles of security. But how does one go about doing this in a simple and productive way?
The secret, as it often is with complex tasks, lies in breaking the task down into manageable parts. This approach doesn’t just make the task more approachable, but it also allows us to focus on individual aspects, ensuring that nothing crucial slips through the cracks.
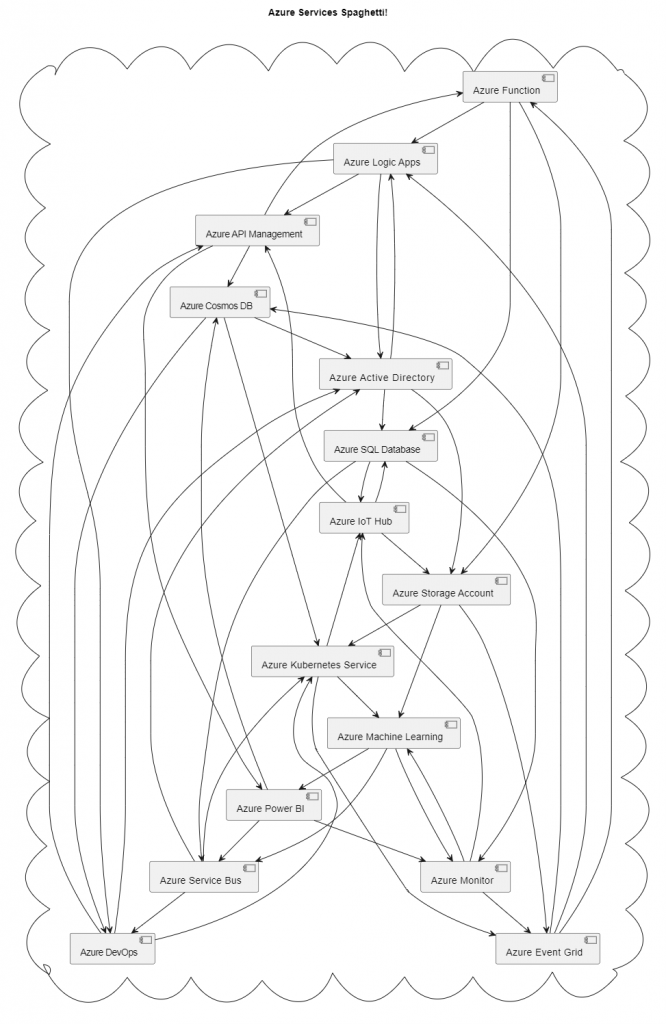
As a practical example, consider a use case for a banking institution that leverages various Azure services.
Our hypothetical banking institution wants to implement a real-time fraud detection system that monitors transactions, evaluates them for potential fraudulent activity based on certain risk factors, and alerts the bank’s security team for any suspicious transactions.
- Azure Event Grid: This service is used as the event routing service that dispatches events from different sources (in this case, the bank’s transaction systems) to the relevant handlers. The transaction data is published to the Event Grid each time a transaction is made.
- Azure Service Bus: Acts as the messaging intermediary, enabling a secure and reliable communication channel between the transaction systems and the rest of the architecture. The transaction data from the Event Grid is forwarded to the Service Bus.
- Azure Logic Apps: This cloud service is used to orchestrate and automate the workflow. Logic Apps receives the transaction data from the Service Bus, performs an initial filtering to eliminate transactions that fall below a certain risk threshold, and then forwards the high-risk transactions to the Azure Function for more intensive processing.
- Azure Function: Azure Function, a serverless compute service, hosts the fraud detection algorithm, which could be a machine learning model trained to identify fraudulent transactions. The function processes the transaction data, scores it based on the likelihood of fraud, and stores the result in the Azure SQL Database. In cases where the score exceeds a predetermined fraud threshold, the function triggers an alert and pushes it to a queue in the Service Bus.
- Azure SQL Database: This fully managed relational database service stores the details of the transactions, their associated risk scores, and the results of the fraud analysis. This data can be used for audit, analysis, and reporting purposes.
- Storage Account: Azure Storage provides a place to store logs, reports, and other data. For instance, the raw transaction data for long-term archival, or the logs generated by the various components of the architecture for monitoring and troubleshooting purposes.
- API Management: This fully managed service handles the APIs that expose the banking services to external applications. It provides a secure, scalable, and reliable entry point for the transaction systems to publish transaction data to the Event Grid. It also serves as an interface for the bank’s security team or other internal systems to query the results of the fraud analysis from the Azure SQL Database.
- Azure Monitor: It is used to monitor the performance and availability of all the Azure services used in this architecture. It collects, analyzes, and acts on telemetry data, helping to ensure that the system is functioning correctly and to rapidly diagnose any issues that occur.
Below a diagram of our cloud architecture:
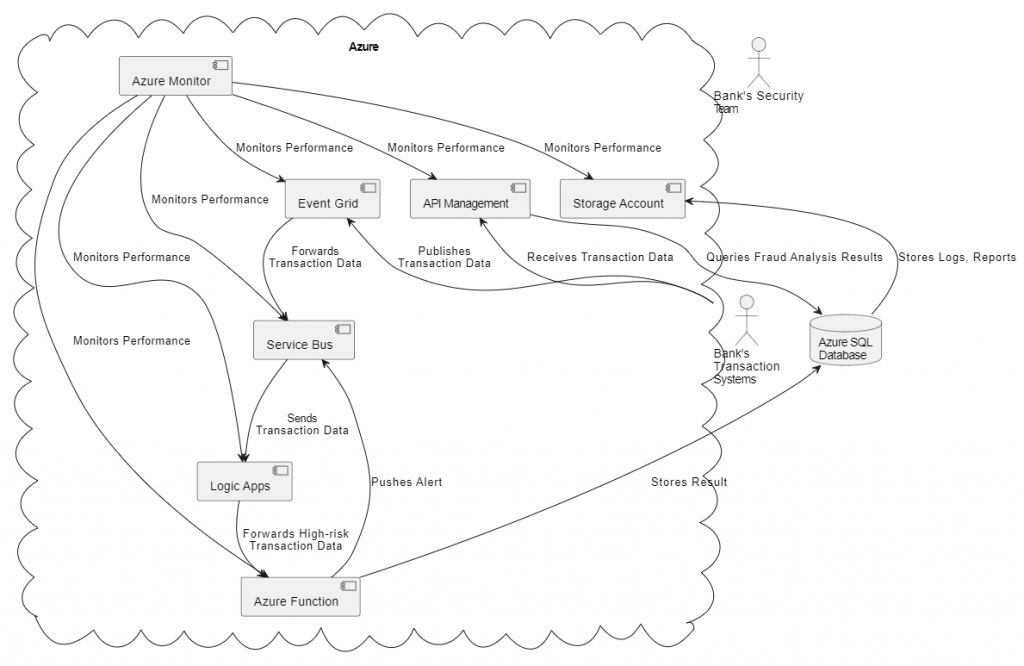
The current architecture seems functional, but it appears to lack the foundational principles of the CIA triad. It leads me to question – how could an architect design it without incorporating these essential security considerations? I believe it’s nearly impossible to create a reliable and secure design without these principles.
To me, it’s not solely about security. The application of the CIA triad principles goes beyond that. It’s about building a robust, reliable, and resilient cloud architecture. Without incorporating Confidentiality, Integrity, and Availability at its core, I firmly believe that it’s nearly impossible to establish a cloud architecture that can truly stand the test of time and varied operational demands.
Let’s proceed to incorporate the CIA triad principles into the architecture components. For instance, we can begin by examining each component individually and classifying them according to the principles of Confidentiality, Integrity, and Availability.
Here’s an illustrative outcome of that process.
Azure Event Grid
- Confidentiality (High): Leveraging Azure Active Directory (AAD) and role-based access control (RBAC), we can strictly control who has the ability to publish and subscribe to events, ensuring a high level of confidentiality.
- Integrity (High): Event Grid’s capability to maintain the sequence of events assists in preserving data integrity. Moreover, using a hashing algorithm to cross-verify that data remains unchanged during transit is another method to uphold high integrity.
- Availability (High): The application of geo-disaster recovery and failover groups with Event Grid significantly contributes to high availability.
Azure Service Bus
- Confidentiality (High): By enabling data encryption both at rest and in transit, and by employing shared access signatures (SAS), we can uphold high confidentiality.
- Integrity (Medium): The native message sequencing and duplicate detection features provided by the Service Bus can maintain medium integrity.
- Availability (High): Higher availability is achieved by enabling Service Bus Geo-disaster recovery and using paired namespaces.
Azure Logic Apps
- Confidentiality (Medium): Logic Apps offers IP restrictions and employs managed service identities (MSI) for secure access, providing medium confidentiality.
- Integrity (Medium): Through the use of workflows designed to handle exceptions, errors, and retries, we can achieve medium integrity.
- Availability (High): The automatic scaling feature of Logic Apps ensures high availability, further improved by geo-distribution.
Azure Function
- Confidentiality (High): The implementation of AAD and RBAC restricts access, while SSL/TLS usage secures data transmission, providing high confidentiality.
- Integrity (Medium): Proper function bindings, triggers, and error handling with retry policies can ensure medium integrity.
- Availability (High): High availability can be achieved through configuring automatic scaling and multiple instances.
Azure SQL Database
- Confidentiality (High): The use of Azure’s Advanced Threat Protection and Always Encrypted with secure enclaves provides high confidentiality.
- Integrity (High): Azure SQL’s built-in support for ACID transactions and data auditing are effective ways to maintain high data integrity.
- Availability (High): The utilization of automatic backups, failover groups, and geo-replication ensures high availability and disaster recovery.
Azure Storage Account
- Confidentiality (High): The Azure Storage Service Encryption (SSE) and secure access via SAS or AAD RBAC provide a high level of confidentiality.
- Integrity (Medium): Azure’s built-in data replication ensures a medium level of data integrity.
- Availability (High): The implementation of Read-Access Geo-Redundant Storage (RA-GRS) contributes to high availability and disaster recovery.
API Management
- Confidentiality (High): The use of client certificate authentication to secure access and enforcing SSL/TLS for data transmission offers a high level of confidentiality.
- Integrity (Medium): Policies for input validation and transformation safeguard the integrity of data flowing through APIs at a medium level.
- Availability (High): Deploying API Management instances in multiple regions and configuring automatic scaling provides high availability.
Azure Monitor
- Confidentiality (Medium): Employing AAD and RBAC for secure access ensures medium confidentiality by controlling who can view and manage logs.
- Integrity (Medium): Using Log Analytics and Azure Security Center to analyze logs helps detect threats that could compromise the integrity of Azure resources.
- Availability (Not Applicable): As Azure Monitor is a monitoring service, specific availability configurations are not necessary.
The application of the CIA triad principles to every element of our cloud architecture, conducted systematically and uncomplicatedly, can considerably illuminate and simplify the architecture design process.
Let’s now take a look at our architecture subsequent to this exercise.
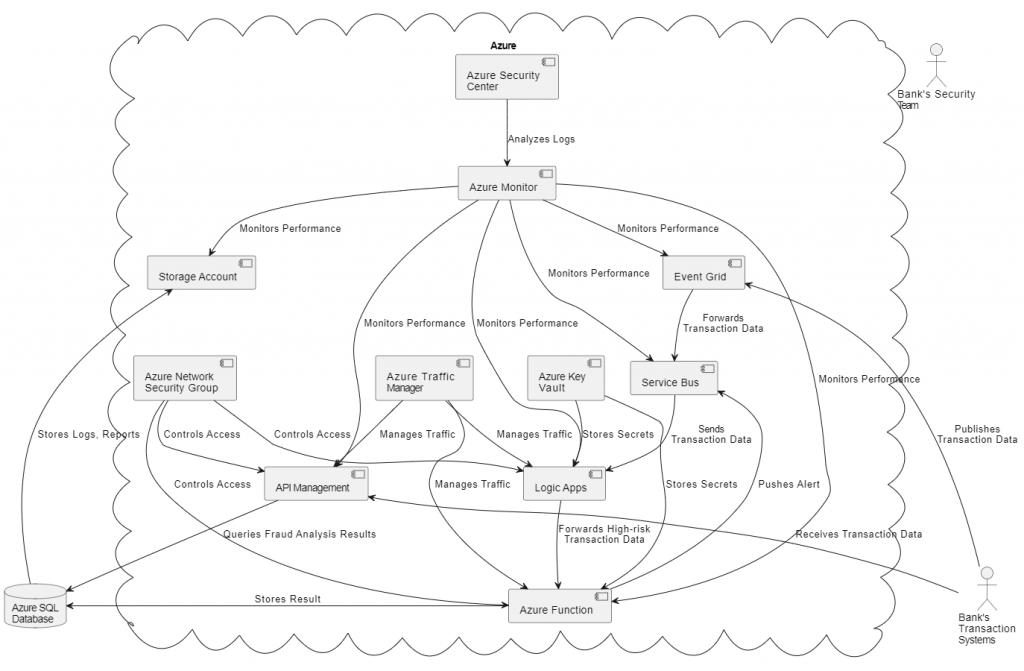
It becomes evident that the systematic and simplified application of the CIA triad to each component of the cloud architecture provides a clear and concise blueprint of how the architecture should be designed. This approach reduces complexity, increases understanding, and streamlines the design process, enhancing the overall architectural integrity and robustness.
As seen in the redesigning of the Azure cloud architecture, the incorporation of the CIA triad has led to significant modifications. The CIA triad has been instrumental in helping us reassess each component from the perspective of Confidentiality, Integrity, and Availability. It has guided us in selecting the right technologies, in the right measure, to meet the CIA principles. This has reshaped the architecture drastically and has taken it a notch higher on the security ladder.
The use of the CIA triad is not just a good-to-have but is a must when it comes to cloud architecture design. By aligning every design aspect with the CIA principles, we are ensuring a robust, secure, and efficient architecture that can confidently meet various operational requirements. Not only does it provide a holistic security view, but it also paves the way for an architecture that can adapt to evolving business needs while maintaining its core security structure.
In conclusion, the importance of the CIA triad in cloud architecture design cannot be overstated. Its strategic application allows architects to ensure their designs are robust, secure, and reliable. It serves as a guiding principle to navigate the complexities of the cloud, highlighting potential vulnerabilities, and providing solutions to mitigate them.
For those interested in delving deeper into the subject, I invite you to refer to my handbook, “Practical Security Handbook: Surviving and Thriving in Azure AIS with the CIA Triad”.
This comprehensive guide provides practical, hands-on advice and detailed explanations about the implementation of the CIA triad in Azure architecture.
Lastly, should you require more personalized guidance or have any queries, feel free to reach out to me.
I offer consultancy services and would be more than happy to assist you in understanding and implementing the CIA triad principles in your cloud architecture designs. Remember, in the world of cloud architecture, security isn’t an afterthought but a primary design principle.
So let’s make our cloud architectures secure, efficient, and resilient with the CIA triad!

