In the last period, I have been working on several projects, most of which required strong hybrid integration with the cloud, others more related to migration and cloud enablement.
Any project or company is different from another, with different requirements, different politics, and different ways to approach delivery and especially security.
In this series of articles, I would like to elaborate on the ten most important tips I have been able to group.
The way companies look at security has always been a very interesting point of reflection. I see some common patterns across all of them. For instance, many of these companies look at security as the last topic of discussion.
Sometimes I have been very surprised by the complete lack of security culture in the company itself, I remember a day when I was discussing with a CTO the importance of closing any 3389 RDP port access to any VM in the cloud for development. The answer he gave me was, “I don’t see any problem with this, we can rebuild the VM again”. I was shocked by this answer, and he was the CTO!
Later I was not surprised to see a lot of many other security problems in the company in many other areas like delivery, process, deployment and development, and here is my first tip.
Tip number one, “Understand security first.”

When we think about security, we immediately think about protection, and I think this is quite understandable behaviour, we relate security to something that is going to protect us.
In real life, we see a policeman, and we feel safer, we install a multi-lock door in our home, and we close it to feel safer, it is almost a common pattern in our mind.
We actually don’t have a clear idea about the real threat. What we know is that the more security measure we use or have, and better it is.
The same thing is in IT, we close ports with a firewall, and we encrypt data, but how much do we really know about what is happening around us? Do we have a clear idea about the threats?
We are living in a world where information technology is considered the nerve of that, we are all interconnected, and technology is now an integrated part of our real life, and we cannot ignore that. Cyber-attacks are happening everywhere, targeting companies and people. We can see all of that using real-time cyber maps such as Kaspersky cyber map.
https://cybermap.kaspersky.com
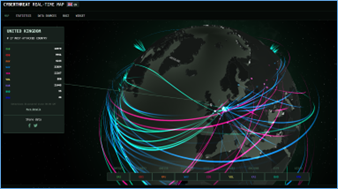
The Kaspersky cyber map is just one of many others. I like it because of the very nice graphical way of representing our real world.
You can find here a list of many others.
https://cybersecuritynews.com/cyber-attack-maps
It is quite impressive to see in real all these attacks, these attacks are happening in real time, and it actually looks like a war.
Security is a global problem, and it is war across our world, and we cannot ignore that.
We cannot protect ourselves and our company from everything, this is impossible. I always like to tell people, “don’t do security for the sake of security, do security for the sake of your company”, but this is another tip that we will discuss in another article.
One first thing we need to do is start by understanding the most common and used attacks we can face, at this point, Microsoft released a very interesting report showing the most common attacks by price.

You can find more detailed information at this interesting workshop
https://learn.microsoft.com/en-gb/security/ciso-workshop/the-ciso-workshop
Why is this important?, this diagram gives us a clear picture of the cheapest attack type, and you can quickly make your conclusions about that.
As you can observe from the diagram, attacks like DOS, and fishing are very cheap, and it is impressive to see the price for a ransomware attack is extremely cheap.
This diagram is good for thinking about the priorities we need to handle first. There is no point focusing on protecting from zero-day attacks first, which is something extremely expensive to conduct or to pay for.
Yes, you are thinking right, there is a black market where people can hire even an army of cybercriminals, and they have extremely advanced organizations and trained people able to conduct a very complex attack easily.
Notice I used the term cybercriminal because this is another important thing to understand. In my opinion, people are completely confusing the difference between a cybercriminal and a hacker.
Hacker is a person able to think outside the box, a black hacker is not a criminal, a black hacker is a security technology expert breaking into a system without the specific authorization of the target, and this is not necessarily conducted for malicious scopes.
A cybercriminal is just a criminal attacking a target for criminal offence scopes, he does that for money or to hurt people, to damage, or for terrorism purposes.
It is important to start calling them criminals and not hackers, and this is making us aware of the real threat.
The last important aspect to understand is technology.
Below the cybersecurity reference architecture provided by Microsoft.
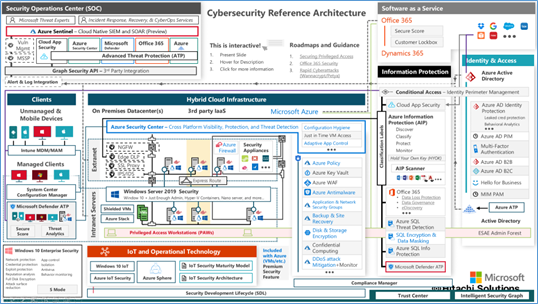
It is impressive the number of technologies, today we really have very advanced software capable of intercepting threats in real-time, monitoring any type of strange anomaly using AI, and more.
There are two important considerations to make and understand here. The first consideration is that we now have a very powerful out-of-the-box shield built around our solutions in the cloud. Attaching a system is not as easy as just ten years ago, a brute force attack is almost impossible, decrypt data is a very expensive operation requiring a lot of money, hardware and time.
So it looks like we should be protected enough against cybercriminals, right?
Well, this is where we need to understand a very important last thing about security, what we have is just technology to use, and technology does not mean security, technology is just something we can use to solve a security problem.
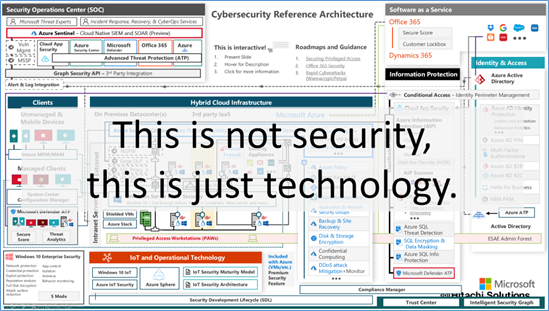
Cybercriminal does not attack technology, they attack people because people are the most vulnerable and easy target to attack.
We need to see and understand security in layers, the same as an onion with different layers, in this case, we need to consider three main layers, and the technology is the very last internal layer.
The three main layers are People first, Process second and Technology the third.
It is impossible to protect our company if people are not on board with the security practices and after our processes.
I remember a phishing campaign in a big company where more than 50 people clicked the link, I remember a CEO sending an email to warn the employees about ignoring his messages from Whatsapp because they were fakes, and his account had been hacked.
Even companies like Solarwind have been hacked, and we are speaking about companies with very strong security policies in the process of delivery.
So here the tip number two, “The success of the technology depends on the people and the process.”
I will speak about this very important tip in my next article, and I will also provide you with a very interesting experiment to conduct in your company, “The chaos monkey experiment.”

