Cybersecurity incidents are dramatically increasing in the last two years, and this is due to many reasons, like politics, social and economic dynamics between countries, the incredible and uncontrolled raising of new technologies and more.
I am very interested in the dynamics governing the cybersecurity gloom around the world, and I like to look at some of the statistics which, in my opinion, can provide some good insights.
Below is one of my favourite slides of all time. It is a slide I saw during a presentation at a Microsoft event.
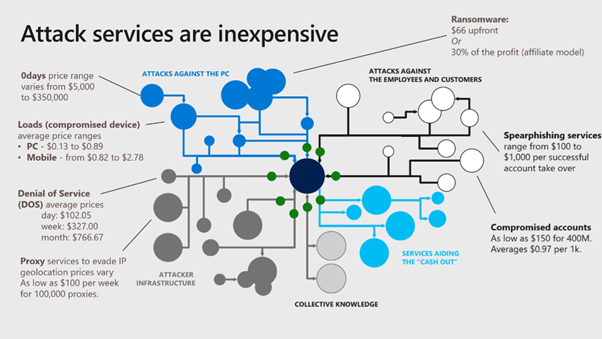
The slide above reports the average cost of the most used attacks, and I was shocked by the low cost of such dangerous attacks. It is also interesting to see that, because they are so cheap, they are also the most frequent attacks we see around.
Last week Sweden was hit by several cyber-attack. Most of the attacks are related to distributed denial-of-service (DDOS) attacks, says Shahid Raza, Director of the Cybersecurity Unit at Rise, Research Institutes of Sweden.
I also examined some of the facts because I like to understand how the attack happened and which possible offence tactic has been used, and I would like to offer some points of reflection about this fact.
“In computing, a denial-of-service attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a network. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.”
rif. Wikipedia
DDOS attack is a quite simple type of attack to conduct, you don’t need to be an expert in offence security, and there are plenty of software and tools available on the internet. A decent gaming computer and decent bandwidth can easily create some serious issues for a website.
Because it is so easy and cheap, the DDOS attack is wildly used everywhere, so my point here is, why companies and organizations are still a victim of this type of attack?
Protecting the endpoints against DDOS attacks is easily achievable with the proper architecture and software design, using the right technology platform, and applying a correct security baseline.
There is nothing magic or complicated behind a DDOS attack, and if this happens, it is because the software solution is not well designed and a correct security baseline is not in place, but there are also other important information coming from the attack.
“TT, a national news agency in Sweden, reported customers who tried to log into the SAS app were logged onto the wrong accounts and had access to the personal details of other people.”
“Scandinavian Airlines (SAS) was hit by a cyberattack Tuesday evening, knocking its website offline and leaking customer data from its mobile app.
During the attack, some travellers who attempted to log into their SAS accounts discovered that they had access to the personal information of other customers, including their names, dates of birth, postal address, email address, and details of previous and upcoming flights.”
These things are confirming me that the attackers also exploit the API stack in the solution.
“An application programming interface (API) is a way for two or more computer programs to communicate with each other. It is a type of software interface, offering a service to other pieces of software.[1] A document or standard that describes how to build or use such a connection or interface is called an API specification. A computer system that meets this standard is said to implement or expose an API. The term API may refer either to the specification or to the implementation.”
rif. Wikipedia
Broken Object Level authorization (BOLA) and Broken function Level authorization (BFLA) is the classic API vulnerabilities capable of producing the behaviours experienced by the users during these attacks.
Below are very interesting statistics from nordicapis.com that will provide us with some very interesting and, for some people, shocking revelations, starting from the most shocking one:
- 83% of All Internet Traffic Belongs to API-Based Services
- There Are Over 2 Million API Repositories On GitHub
- 93.4% of API Developers Are Still Using REST
- According to the State Of The API Economy report, 56% of developers find APIs help build better digital products. They also feel that APIs:
- Accelerate Innovation (52%)
- Integrate Systems (40%)
- Create Business Value (36%)
- Are Products Themselves (22%)
- Cloud Automation Will Become a $623.3 Billion Industry By 2023
- Healthcare APIs Are Growing By 6.3% CAGR
- Open Banking to Have 130 Million Users by 2024
Financial services are some of the largest adopters of API-related technology
rif. nordicapis.com
Not many people realize that behind any application, software, website, or mobile app we use, there are hundreds or thousands of APIs.
The majority of companies, also security companies, are very focused on the UI security aspect, and they underestimate the huge impact and importance of APIs.
I am conducting a lot of research and study across offence API Security, and it is a very complex topic. Attack APIs is a completely different matter from the classic “WWW”, and it requires a totally different approach.
There are top 10 API Security vulnerabilities, and they are focused on several aspects of the API lifecycle and space. I think BOLA (Broken Object Level Authorization) and BFLA (Broken Function Level Authorization) are some of the most frequent with Excessive Data Exposure. Other important vulnerabilities are Broken User Authentication, Lack of Resources & Rate Limiting ,Mass Assignment, the classic and infamous Security Misconfiguration, the famous and omnipresent Injection (which includes code and the SQL one), for the DevOps guys Improper Assets Management and the Insufficient Logging & Monitoring.
I encourage you to go through the links to read more about these interesting vulnerabilities.
If you like to attack API and understand more about these vulnerabilities, I recommend the completely ridiculous API (crAPI) and the Vulnerable Adversely Programmed Interface (vAPI).
In the next period, I have in a program to speak more about the red side of API security and also provide specific training about it.
It is important for companies to be more aware of the importance of this crucial technology stack. If you know the way to compromise an API, you will also know how to better protect APIs and how to write code in API in the correct way to avoid vulnerabilities and dangerous attacks.
Stay tuned!

