The CIA triad is a fundamental cornerstone for ensuring robust security in API design. By applying the principles of Confidentiality, Integrity, and Availability to the areas of Transport, Application, Data, Code, and Policy, we can build and maintain APIs that are not only functionally efficient but also secure and reliable. Microsoft Azure provides an array of services that can aid in achieving these objectives in each area, making it a powerful tool for any organization aiming for secure and efficient API implementation.
The CIA triad is a foundational concept in information security.
It stands for:
Confidentiality: Ensuring that data is accessible only to those authorized to have access.
Integrity: Safeguarding the accuracy and completeness of data during its lifecycle.
Availability: Ensuring that data is accessible and usable upon demand by an authorized entity.
When it comes to API (Application Programming Interface) design, the CIA triad is very important.
Here’s why:
Confidentiality: APIs often deal with sensitive data, and it’s crucial that this data only be accessible to authorized users. This is why we use techniques such as token-based authentication, OAuth, or JWT to verify the identity of users before they can access the data.
Integrity: When data is sent or received via an API, it’s important that it isn’t changed in transit. This is where HTTPS and other secure communication protocols come in, as they ensure the data sent is the same as the data received. APIs should also have error-checking mechanisms to verify the integrity of incoming data.
Availability: APIs must be reliable and always available for use when needed. This means the underlying systems must be robust and resilient, able to handle large volumes of requests and recover quickly from failures. Techniques like load balancing, rate limiting, and redundancy can help ensure availability.
So, while the CIA triad might not be directly referenced when people talk about API design, the principles it embodies are absolutely critical to building secure, reliable APIs.
It’s always important to consider these aspects in any system that involves data transfer or storage, and APIs are no exception.
The CIA triad must be applied across all areas of API design to ensure secure and reliable operations.
I identified five main areas in the API lifecycle, Transport, Application, Data, Code, and Policy.
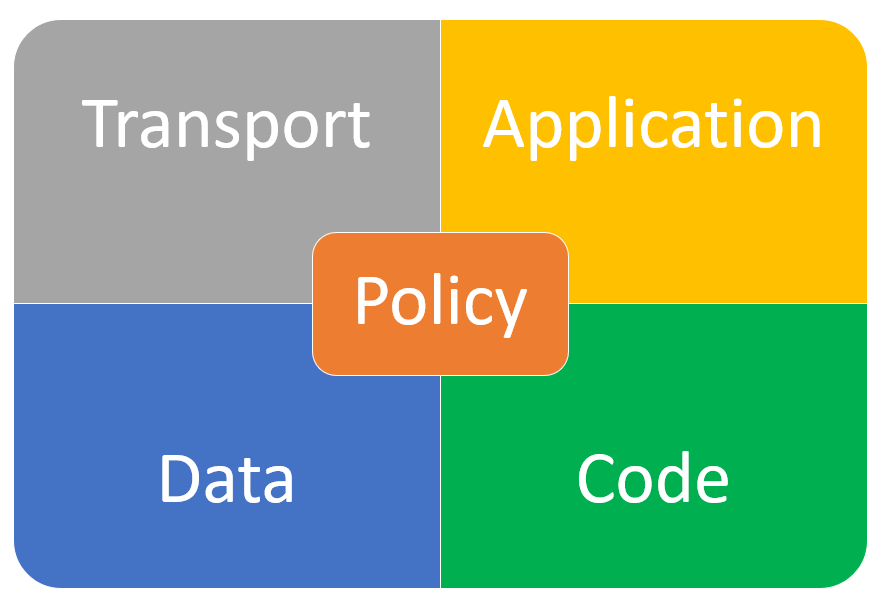
Transport
This concerns how data is moved between client and server.
Confidentiality can be ensured using protocols like HTTPS, which encrypts data during transmission. Integrity can be ensured through techniques like hashing and digital signatures that help verify the data hasn’t been tampered with in transit. Availability is about ensuring the service is always accessible, for example through the use of load balancing. Azure technologies that can help include Azure Load Balancer and Azure Traffic Manager for availability, and Azure Application Gateway for secure HTTPS transport.
Below are the essential actions and technologies to consider for each area:
Confidentiality
- Use HTTPS and Implement TLS: Always use HTTPS for secure data transmission. Azure Application Gateway can enforce HTTPS for data transmission. It also provides a Web Application Firewall (WAF) that protects your applications from common web vulnerabilities and exploits.
- API Keys: Azure API Management can help manage and secure access to your APIs using subscription keys.
Integrity
- Data Integrity Checks: Azure Application Gateway, by enforcing HTTPS, helps ensure that data is not tampered with during transport.
- Secure Communication Protocols: As mentioned, Azure Application Gateway provides secure communication through HTTPS and TLS protocols.
Availability
- Load Balancing: Azure Load Balancer and Azure Traffic Manager can distribute network traffic evenly across several servers, increasing your API’s availability.
- Redundancy: Azure provides several services to ensure redundancy, such as Azure Traffic Manager, which can perform automatic failover to ensure high availability.
- Rate Limiting: Azure API Management provides features for rate limiting to protect your API from being overwhelmed by too many requests.
Application
This refers to the API code itself.
Confidentiality can be maintained by ensuring only authenticated and authorized users can access certain endpoints. Integrity can be ensured by validating input data and output data. Availability involves things like error handling and redundancy to ensure the API remains available even if a component fails. Azure Active Directory can be used for authentication and authorization, while Azure Functions or Azure App Service can help ensure availability.
Let’s now consider how to apply the CIA triad to the Application layer of API design, and which Azure technologies can help:
Confidentiality
- User Authentication: Ensure that only authenticated users can access your API. Azure Active Directory (Azure AD) provides identity and access management services, enabling strong authentication mechanisms.
- User Authorization: Control what each authenticated user can do. Role-based access control (RBAC) in Azure AD can be used to assign permissions to users, groups, and applications at a certain scope.
Integrity
- Input Validation: Check all data coming into your API to ensure it’s in the right format and makes sense in your context. Azure Functions or Azure Logic Apps can be used to implement such checks.
- Output Validation: Similarly, make sure the data your API sends out is accurate and reliable. This can also be implemented using Azure Functions or Azure Logic Apps.
Availability
- Error Handling and Recovery: Make sure your API can handle errors gracefully and recover quickly from failures. Azure Functions provides built-in error-handling capabilities.
- Scalability: Ensure your API can scale to handle a large number of requests. Azure Kubernetes Service (AKS) and Azure Service Fabric can help deploy and manage microservices to provide scalability.
- Resiliency: Implement strategies to make your API resilient to failures. Azure provides several resiliency design patterns, such as retry, circuit breaker, and compensating transaction patterns.
Data
This involves the data being transferred or stored.
Confidentiality can be maintained using encryption both at rest and in transit. Integrity can be ensured using hashing or checksums to validate the data. Availability is about ensuring the data is always accessible when needed, for example through the use of redundant storage or backup mechanisms. Azure technologies that can help include Azure SQL Database or Azure Cosmos DB for storage, with built-in features for encryption, redundancy, and backup.
Below is how to apply the CIA triad to the Data layer of API design, and the Azure technologies that can help:
Confidentiality
- Data Encryption: Protect your data at rest and in transit. Azure SQL Database and Azure Cosmos DB offer transparent data encryption at rest. Azure also supports encryption in transit using SSL/TLS.
- Access Control: Limit who can access the data in your API. Azure RBAC can provide fine-grained access management for your databases.
Integrity
- Data Validation: Use mechanisms to ensure data integrity such as checksums and data hashing. These can be implemented at the application layer using Azure Functions or Azure Logic Apps.
- Versioning and Change Tracking: Azure Cosmos DB provides features like change feed that can help track changes to data over time.
Availability
- Redundancy and Backup: Azure offers automatic backup and restore features for databases like Azure SQL Database and Azure Cosmos DB. Redundancy can be achieved using replication features available in these services.
- Scalability: To handle high loads, Azure SQL Database and Azure Cosmos DB support automatic scaling.
- Disaster Recovery: Use Azure Site Recovery to orchestrate a disaster recovery plan, ensuring your data remains available in the event of a major incident.
Code
This involves the actual code used to implement the API.
Confidentiality can be ensured by limiting access to the codebase and using obfuscation techniques. Integrity can be ensured by using version control systems and performing regular code reviews and audits. Availability is less directly applicable at the code level, but good coding practices can help ensure the overall availability of the API. Azure DevOps can help with version control and code reviews, while Azure Security Center can provide security recommendations and threat detection.
Below is how to apply the CIA triad to the Code layer of API design and which Azure technologies can assist:
Confidentiality
- Access Control: Limit access to the codebase to only those who need it using Azure DevOps, which provides granular access controls for your source code.
- Code Obfuscation: Protect the intellectual property of your code by making it harder to reverse-engineer. This is more related to the code of mobile applications or client-side JavaScript than server-side API code.
Integrity
- Version Control: Use a version control system to keep track of changes and prevent unauthorized modifications. Azure DevOps provides Git repositories for source control.
- Code Review: Regularly review code for potential security issues. Azure DevOps also supports pull requests which can be used for code reviews.
- Secure Coding Practices: Follow secure coding practices to prevent common security issues. Tools like SonarQube, which can be integrated with Azure DevOps, can help detect potential issues.
Availability
- Continuous Integration/Continuous Deployment (CI/CD): Implement CI/CD to quickly recover from failures and ensure the latest, most secure version of your API is always deployed. Azure DevOps provides robust CI/CD pipelines.
- Automated Testing: Use automated testing to catch issues that could lead to downtime. Azure Pipelines supports running automated tests as part of your CI/CD pipeline.
Policy
This involves the policies and procedures surrounding the use of the API.
Confidentiality can be maintained by having strict policies on who can access the API and how they can use it. Integrity can be ensured by having policies that require data validation and error checking. Availability is about having policies that ensure the API is regularly maintained and issues are quickly resolved. Azure Policy can help enforce and manage policies at scale, while Azure Monitor can help track API usage and performance.
Below is how to apply the CIA triad to the Policy layer of API design, and the Azure technologies that can help:
Confidentiality
- Access Policies: Use Azure Policy to define fine-grained access policies for your API, controlling who can do what.
- Data Classification Policies: Use Azure Purview to classify and label data according to sensitivity. This helps ensure that confidential data is treated appropriately.
Integrity
- Audit Policies: Use Azure Policy and Azure Monitor to regularly audit your API and its usage. This helps ensure that the API is being used correctly and that data integrity is maintained.
- Change Management Policies: Use Azure DevOps to manage changes to the API, ensuring that changes are properly reviewed and approved before being implemented.
Availability
- Disaster Recovery Policies: Use Azure Site Recovery to implement disaster recovery policies, ensuring that your API can quickly recover from a disaster.
- Maintenance Policies: Use Azure Automation to automate regular maintenance tasks, helping to ensure the continued availability of your API.
- Monitoring Policies: Use Azure Monitor to set up monitoring and alerting policies, helping to ensure that any issues that could affect availability are quickly identified and resolved.
By integrating all of these actions with Azure technologies, you can effectively apply the principles of the CIA triad—Confidentiality, Integrity, and Availability—across the Transport, Application, Data, Code, and Policy layers of your API design. As we’ve seen, each layer presents unique challenges and opportunities, but with a thoughtful and systematic approach, it’s possible to build APIs that are secure, reliable, and effective.
However, this is only scratching the surface of a broad and crucial topic. The rapidly evolving landscape of cybersecurity and data privacy means that API designers must continually learn and adapt. From emerging encryption techniques to innovative strategies for data validation, there’s always more to discuss and explore.
In future articles, we will delve deeper into each of these layers, providing practical examples, exploring real-world case studies, and discussing the latest trends and technologies. We’ll also continue to explore how Azure technologies can be leveraged to address these challenges and opportunities, providing you with the tools and knowledge you need to design APIs that not only meet but exceed today’s security standards.
I am personally available for consulting services and to answer any questions you might have about your unique API design needs. Whether you’re dealing with a specific security challenge, or just want to learn more about best practices in API design, I am here to help.
Please don’t hesitate to reach out at any time
I look forward to hearing from you and supporting you in your API design journey.

