Cybersecurity in Microsoft Azure is a multifaceted domain due to the variety of technologies it encompasses from databases and storage accounts to networking. Indeed, this intricacy is necessary to maintain robust security, despite it sometimes seeming somewhat bewildering.
Microsoft has made the cybersecurity landscape more navigable by publishing comprehensive white papers known as the Microsoft cybersecurity reference architectures.
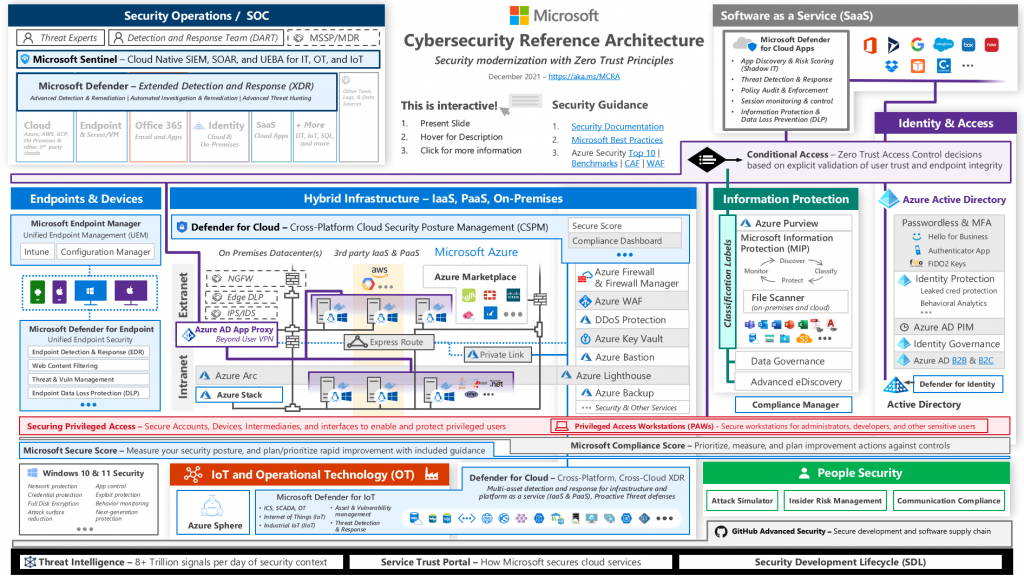
These documents offer diverse architectural blueprints that can be applied to various types of security architecture. Here’s the link to their main security architecture document: Microsoft Security Architecture.
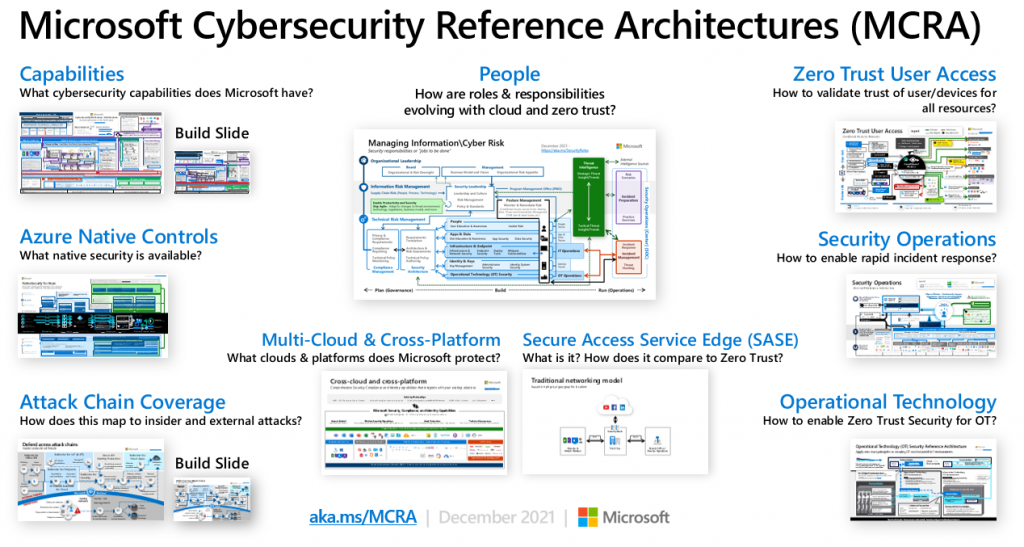
Though the topic may appear overwhelming at first, the purpose of this article is to demystify the complex terrain of Microsoft Azure cybersecurity.
Fundamentally, Microsoft Azure security operates on the principle of zero trust. This principle is divided into three core concepts: explicit verification, least privilege, and assumed breach.
Explicit verification implies that no trust is given based on location or affiliation. Every identity must be confirmed multiple times before access is granted.
The concept of least privilege means that a specific account should have only the necessary permissions for the task at hand, and only when they’re required.
Assumed breach means every activity in the cloud is monitored closely, considering the possibility of a breach. All user or resource interactions with the cloud are thoroughly analyzed for potential threats.
To comprehend Microsoft Azure security better, it’s important to understand the basic principles of authentication and authorization.
Authentication, the critical security measure that ensures the identity of a user or service before granting access, is primarily managed within the Identity Area of Azure Security. This area houses Azure Active Directory (AAD), which verifies identities via multi-factor authentication, conditional access policies, and Identity Protection Risk features. Thus, it serves as the cornerstone of the authentication process in the Azure Security landscape.
Authorization, which is fundamentally the practice of granting permissions to an authenticated user or service, is primarily overseen by Azure’s Infrastructure Security area. More specifically, features such as Role-Based Access Control (RBAC) and Azure Active Directory (AAD), particularly with features like Conditional Access, are instrumental in managing and enforcing authorization policies.
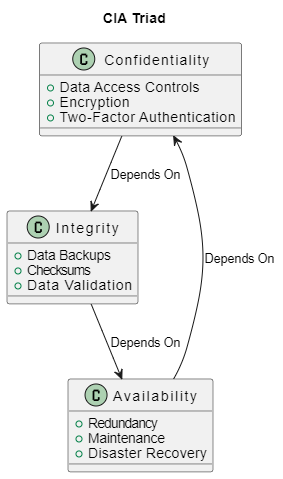
Another essential Security framework to grasp in cybersecurity is the CIA triad, which stands for Confidentiality, Integrity, and Availability. These three principles dictate our approach to security technology and the choice of tools we use. They apply to every aspect of security, whether it’s data, services, individuals, or actions.
- Confidentiality: This means the information is accessible only to authorized individuals. Measures are taken to prevent unauthorized access to data, thus preserving its secrecy.
- Integrity: This principle ensures that the data is trustworthy and accurate throughout its entire lifecycle. It prevents unauthorized alteration of data, ensuring it remains in its original state unless changed by an authorized entity.
- Availability: This principle ensures that data and services are available whenever required. It involves maintaining hardware, performing upgrades, and dealing with potential disruptions.
We can map these principles to objects in the Microsoft Cybersecurity Reference Architecture:
- Confidentiality: Confidentiality is managed by various areas within the reference architecture. The Data Security area, for instance, employs Azure Information Protection and Azure Purview to classify, label, and protect sensitive data, ensuring that only authorized individuals can access it. Moreover, in the Infrastructure Security area, Azure Key Vault is used to securely store and access secrets like API keys and passwords, contributing to the confidentiality principle. Azure Private Link in the Network Security area ensures that access to certain services is private, meaning data travels over a secure, private network connection.
- Integrity: The Data Security area ensures integrity through Azure Information Protection, which restricts the alteration of data to only authorized entities. Azure Backup, part of Infrastructure Security, contributes to integrity by protecting data from unauthorized changes and corruption. In the Network Security area, Azure Firewall and Network Security Groups control access to data and prevent unauthorized alteration.
- Availability: The Infrastructure area plays a critical role in maintaining availability. Azure Resource Manager (ARM) ensures that resources are available and correctly configured. Azure Load Balancer and Azure Traffic Manager, both in the Network area, ensure high availability and scalability of applications by distributing network traffic. Azure Backup and Azure Site Recovery ensure that data is available, even in the event of system failure or disaster. Moreover, the Identity area, specifically Azure Active Directory, manages access control and authentication, ensuring authorized users have access to systems and data when required.
Now let’s return to our diagram and embark on our exploration of the fascinating world of Azure security.
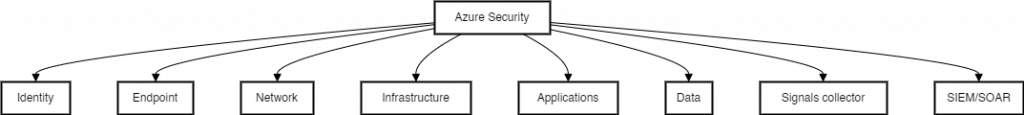
Microsoft Azure security is structured around key areas which are, Identity, Endpoint, Network, Infrastructure, Applications, Data, Signals collector, and SIEM/SOAR.
- Identity: This involves managing and securing user identities. Azure Active Directory is an example of a service that handles this.
- Endpoint: This area focuses on securing devices that connect to the network, such as computers, tablets, and mobile devices.
- Network: Network security involves protecting the infrastructure that allows devices to connect and communicate with each other.
- Infrastructure: This encompasses the systems and services that are used to build, operate, and manage applications, like virtual machines and containers.
- Applications: This involves protecting applications from threats, which can be done by implementing secure coding practices and using application security tools.
- Data: This involves protecting data both at rest and in transit. Azure provides a variety of services for this, such as Azure Storage Service Encryption and Azure SQL Database Always Encrypted.
- Signals: This function gathers data from various sources to monitor for potential threats and anomalies.
- SIEM/SOAR: SIEM (Security Information and Event Management) is used for real-time analysis and reporting of security alerts. SOAR (Security Orchestration, Automation, and Response) is a solution that combines threat and vulnerability management, case management, and incident response into a single platform.
Now, we’re going to explore the various areas and I will help you identify, in a very straightforward and clear manner, the most important parts of this complex diagram. Here’s an exercise I recommend: as you read, try to locate the name of the technology and observe its relationships, let’s start with the Identity area.
Identity
Microsoft Azure Identity is an integral part of Azure security. It utilizes a variety of services and tools to provide secure and seamless authentication and access control.
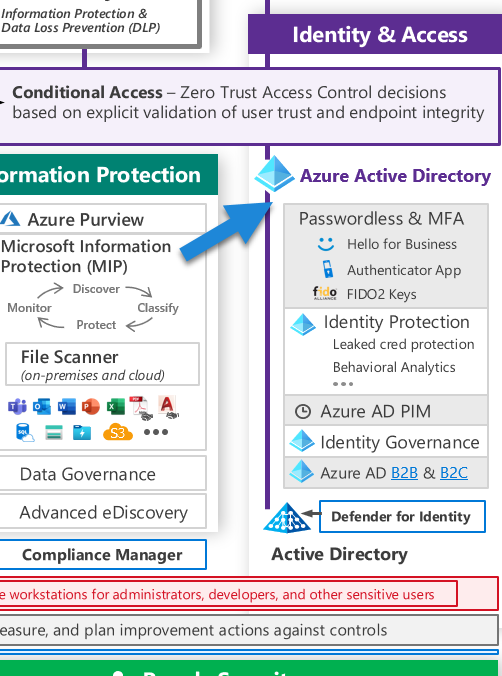
Azure Active Directory (AAD) is at the heart of Azure Identity. It’s an Identity and Access Management (IAM) solution, providing a robust set of capabilities to manage users and groups. It helps secure access to on-premises and cloud applications, including Microsoft’s online services like Office 365 and many others from third parties.
The AAD comes in three tiers: Free, P1, and P2. The Free tier provides Security Defaults, which includes basic features such as user and group management, single sign-on (SSO), and multi-factor authentication (MFA), a vital security feature that adds an extra layer of protection to the authentication process.
The P1 tier enhances these features with Conditional Access and more comprehensive MFA options. Conditional Access is a powerful tool that allows you to enforce policies and rules for accessing your apps based on various conditions, enhancing the security of your environment.
The P2 tier offers Identity Protection Risk features. These offer advanced tools to detect potential vulnerabilities and automate responses to detected suspicious actions related to your identities. The Identity Protection Risk functionality is based on Conditional Access, meaning it utilizes the same framework but offers more sophisticated threat detection.
If you have an on-premises infrastructure, Azure AD Connect is used to synchronize your local Active Directory with Azure AD, thus extending its capabilities to the cloud. This integration enables you to use Identity Protection to safeguard your on-premises identities as well.
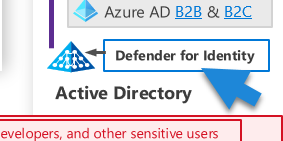
Defender for Identity is another security feature that helps protect your on-premises Active Directory identities. It uses machine learning algorithms to detect suspicious activities that may indicate threats like pass-the-hash, pass-the-ticket, or other types of malicious insider activity.
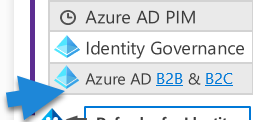
External partners can be integrated using Azure AD B2B (Business-to-Business) functionality, allowing you to share your organization’s applications and services with external partners securely. For customer-focused applications, the B2C (Business-to-Customer) functionality of AAD enables you to provide secure, scalable, and reliable access.
All these components of Azure Identity interact and work together, forming a secure, flexible, and robust identity infrastructure. This infrastructure underpins the security of your applications and data, both in the cloud and on-premises, ensuring that only authorized users have access and that their identities are protected at all times.
Endpoint
Microsoft Azure offers a comprehensive Endpoint management solution to secure and manage devices on your network. This process involves a series of interconnected tools and services that work together to provide protection and oversight.
In the vast landscape of devices and endpoints on your network, Azure Active Directory (AAD) plays a significant role. Devices can be registered in AAD, enabling tracking compliance and the application of various policies. This provides the first level of security control by allowing only compliant and policy-abiding devices to interact with your network.
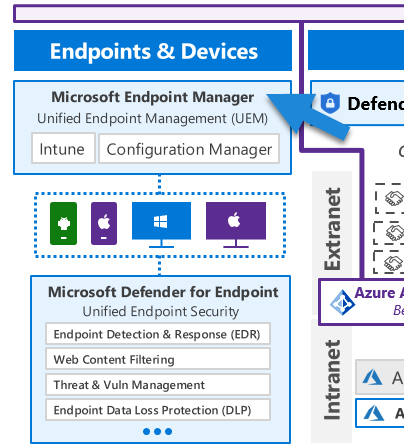
The Microsoft Endpoint Manager (MEM) is a key player in Azure’s endpoint security. It includes Microsoft Intune and Configuration Manager, providing a unified, integrated management platform. This combination facilitates an integrated approach to managing both on-premises and mobile devices.
Under the hood, MEM leverages Azure policies to control the compliance status of our devices. The feedback on compliance status can further inform Conditional Access policies, thus controlling whether a specific access request is permissible.
The policies applied through MEM also enable configuration management and inventory tracking of devices. This makes MEM integral to Azure’s endpoint security strategy and closely ties it to Microsoft Defender for Identity.
Microsoft Defender for Identity and MEM are interconnected through a robust set of policies that coordinate these services. This relationship underscores the crucial role of Azure Policies in maintaining security across Microsoft’s features and technologies. Without them, coordination and control across various Azure services would not be possible. This is why the enabling or disabling of a policy can have broad implications, impacting many security areas in Azure.
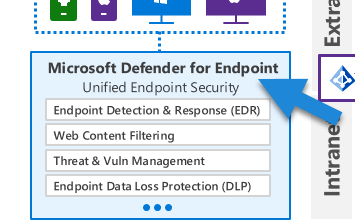
Microsoft’s security suite includes various specialized Defender services, each tailored for specific technology types or areas. For instance, within MEM, we have Defender for Endpoint. It is designed to protect, detect, and respond to threats on your devices. Interestingly, Defender for Endpoint relies on policy compliance to detect abnormalities or security breaches.
Defender for Endpoint includes anti-virus and anti-malware capabilities and utilizes machine learning to identify and respond to potential threats. It’s designed to not only protect against known threats but also to identify new potential risks through pattern recognition and anomaly detection.
Also within the endpoint area, we have Defender for Servers. This security feature uses adaptive application hardening and machine learning to monitor for abnormal behavior in device operations. It also includes file integrity monitoring, which checks for unusual changes in files. If it detects unusual activity or changes, it can block the action and alert your security team.
Azure’s Endpoint security relies on a sophisticated network of interconnected services, technologies, and policies. It provides a holistic, automated, and robust security solution to protect your network endpoints.
Network
The network is the backbone that supports the entire system. Consequently, various security components are dispersed across the landscape, integrated throughout the infrastructure. This intermingling ensures the network’s integrity, maintaining a robust and comprehensive protection system.
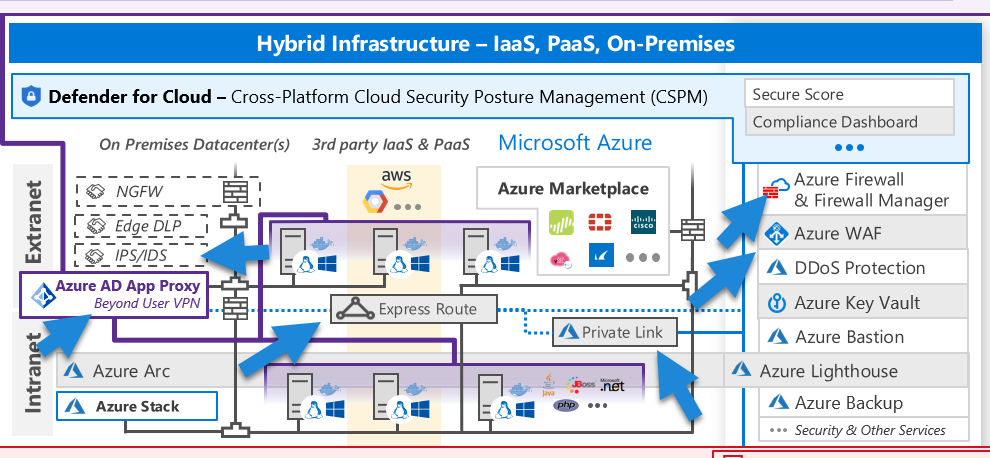
The Azure network infrastructure is founded on the concept of virtual networks, which are subdivided into subnets. Network Security Groups (NSGs) are used to manage access within these subnets. NSGs function at the network layer (layer 4), and they consist of sets of rules that regulate network traffic. These rules are instrumental for the Endpoint Protection for servers, which uses adaptive protection hardening to suggest network hardening measures, such as closing specific ports or flagging suspicious network traffic.
At the application layer (layer 7), Azure provides the Azure Firewall, which is deployed within a subnet. This firewall can perform tasks like TLS inspection and threat detection. The firewall can be extended and controlled through User Defined Routes (UDR) to manage network traffic.
Public traffic is typically handled by the Azure Front Door (AFD), another layer 7 service that provides global coverage. It offers HTTPS management, Content Delivery Network (CDN) capabilities, custom rules, and more. AFD can be fortified with a Web Application Firewall (WAF), which protects against the top 10 OWASP vulnerabilities in HTTPS communication.
While AFD is a global service, the Application Gateway provides similar services at a regional level and can also be fortified with a WAF. AFD and Application Gateway are focused on HTTP/S protocols. For other protocols, Azure Traffic Manager manages global traffic while Load Balancer handles regional traffic.
The network area also encompasses Distributed Denial of Service (DDoS) protection, with both free and standard tiers. The free tier offers protection against large-scale DDoS attacks, while the standard tier provides more detailed protection for specific internal IPs and other features.
Service Endpoints in Azure allow services to be defined as rules that can be applied to a firewall. On the other hand, Private Endpoints are a more advanced type of endpoint, limiting traffic to a service from a specific private IP. This allows for more secure connections, like Site-to-Site VPN and ExpressRoute private peering.
However, Private Endpoints only provide one-way communication to the service. If two-way communication within the VNet is required, VNet Integration is used. To deploy app services within a VNet, you can use the App Service Environment v3. By doing this, your services operate within the VNet, simplifying the overall setup and reducing the need for complex configurations.
Infrastructure
The Infrastructure area forms a substantial part of the Azure environment.
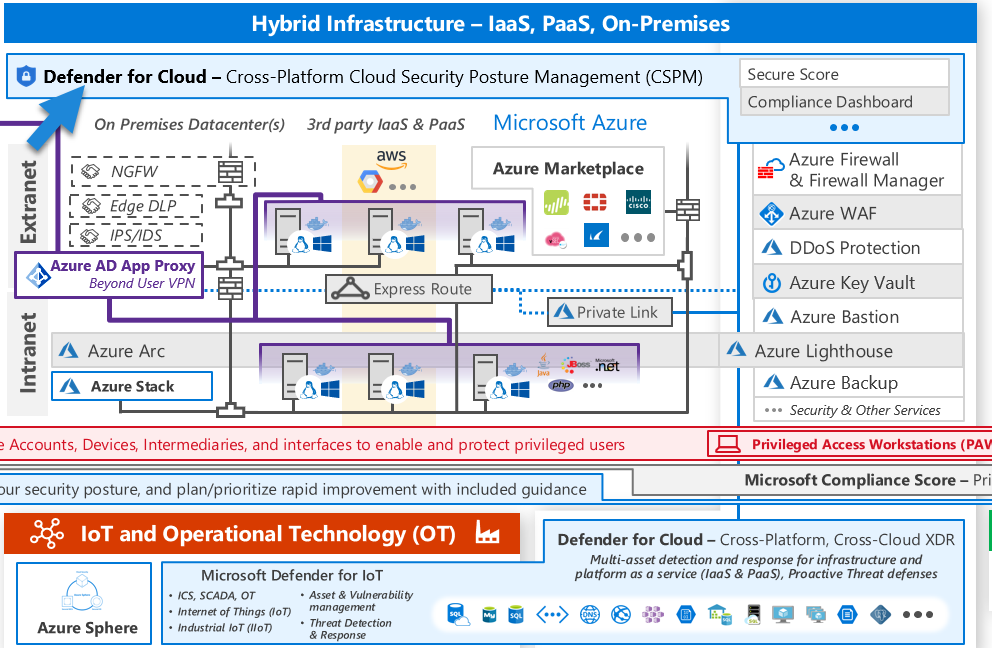
At the helm of this domain is the Defender for Cloud, providing a range of features such as compliance checks, recommendations, and secure posturing. Defender for Cloud allows the implementation of security frameworks like ISO 27001, NIST, Azure CIS, and others. These frameworks comprise vast sets of policies applied at the subscription or management group level, contributing to the Defender’s ability to provide security benchmarks, recommendations, and more. Again, we see the indispensable role of policies in Azure security, indicating how the entire system hinges on them. Interestingly, Defender for Cloud can be extended to other cloud platforms like AWS and Google Cloud.
Azure Policy is the foundation for governing the infrastructure. Meanwhile, Blueprints are utilized to stamp, apply, and verify policy deployment, RBAC rules, and templates. Then we have Azure Key Vault, a tool for managing secrets, keys, and certificates. Key Vault plays a critical role in various security aspects, from storing and controlling access to secrets like API keys, passwords, and certificates, to providing secure means for applications to access sensitive data without exposing it in code.
Virtual machines (VMs) are a vital part of the infrastructure, and Azure offers dedicated security features for them, like Azure Bastion, which facilitates secure HTTPS RDP communications.
The principle of least privilege is upheld in this domain via Role-Based Access Control (RBAC) and Just-In-Time (JIT) access, a feature of Defender for servers. JIT access grants permissions for specific durations, further complemented by Privileged Identity Management for temporary privilege escalations.
Managed Identity helps protect inter-service communication. It comes in two types: System-assigned (managed by Azure and assigned to a single resource) and User-assigned (managed by the user and can be assigned to multiple resources). Managed Identities enable services to authenticate without the need to exchange tokens or sensitive user information.
Azure Resource Manager (ARM) is fundamental to all infrastructure operations and relies heavily on policies for security checks during these operations. You can extend ARM’s capabilities, especially for security, to manage other cloud types and on-premise environments with Azure Arc.
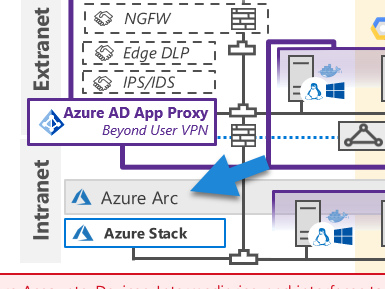
Azure Arc facilitates the deployment of Defender for Cloud’s capabilities across other cloud services and on-premise systems by provisioning agents. This illustrates the power of Azure Arc in extending Azure management and security capabilities to different environments, thus unifying security management across multi-cloud and hybrid cloud setups.
At the base of the diagram, and part of Infrastructure, we find GitHub Advanced Security, which is vital for securing DevOps processes.

This service can analyze code to detect vulnerabilities, playing a proactive role in identifying and mitigating potential security issues before they cause harm. By doing this, GitHub Advanced Security ensures the security and integrity of the code base, reducing the risk of vulnerabilities being exploited in a live environment.
Speaking about Supply Chain and DevOps, at the bottom we have Microsoft Defender for IoT which is a security solution that’s designed to help organizations secure their Internet of Things (IoT) and Operational Technology (OT) devices.
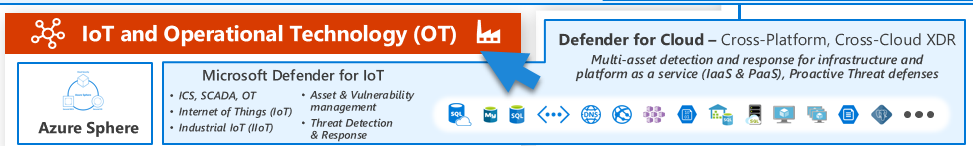
These could include everything from smart thermostats to industrial control systems. Defender for IoT works by identifying the devices on your network, detecting any anomalous behaviors or potential vulnerabilities, and providing alerts and recommendations to help mitigate risks.
We also have Microsoft Defender for Containers which, on the other hand, focuses on the security of container-based applications. Containers are a popular method for deploying applications because they are lightweight and provide a consistent environment across different stages of development. Defender for Containers helps protect these applications by detecting and preventing threats, identifying vulnerabilities in your container images or configurations, and providing visibility into the activities within your containers.
When we talk about their relation with Azure Infrastructure security, both Defender for IoT and Defender for Containers play crucial roles. Infrastructure security in Azure is about ensuring that the foundational elements of your cloud environment, such as your networks, servers, and databases, are secure.
Defender for IoT contributes to this by securing your IoT devices, which may form an integral part of your infrastructure, especially in scenarios like smart buildings or industrial automation. Defender for Containers contributes by securing your containerized applications, which can be a significant portion of your server infrastructure if you’re using microservices or other container-based architectures. By providing security capabilities for these specific aspects of your infrastructure, both services help to enhance the overall security posture of your Azure environment.
Signals
The Signals area is another essential component of the Azure security ecosystem.
Every service sends signals to Conditional Access (CA), and this is why you see this service covering all way long the diagram.
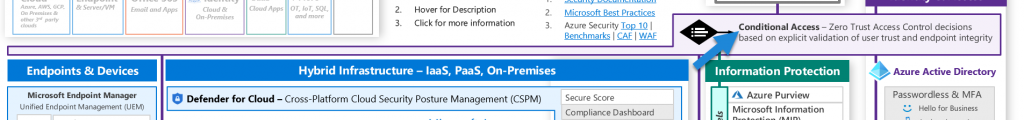
CA is a unique service part of Azure AD Premium P1. Conditional Access, being the central hub for these signals, oversees access to everything inside and outside Azure. It offers the capacity to implement a wide range of policies and rules.
Conditional Access also governs access to apps, extending even to Software as a Service (SaaS) offerings like Office 365. Another layer of security for SaaS applications is provided by Defender for Cloud Apps, which integrates with these apps via APIs to monitor their security. This tool provides detection and alerting capabilities for these apps, and it can also assess the risk scores of many external apps.
Hence, Conditional Access holds a central and critical position in the overall Azure security framework. It’s where all the signals from different services are collected and evaluated according to the set policies, providing a consistent and unified security control mechanism across Azure’s vast ecosystem.
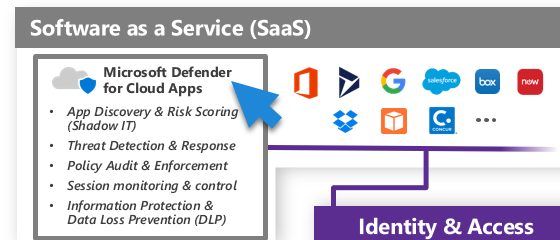
Conditional Access offers a wide range of control capabilities, but what’s truly exceptional is its ability to manage applications. We have the option to integrate our applications with Azure Active Directory (AAD). This is where Microsoft Defender for Cloud Apps plays a pivotal role.
Microsoft Defender for Cloud Apps is a security solution that helps extend the protection of your cloud applications. It provides visibility into your cloud applications and services, provides sophisticated analytics to identify and combat cyber threats, and enables control over data travel. So, in simple terms, it’s like a security guard for your cloud applications, making sure everything is safe and under control.
Other parts of Signals area is People security and, as I always say, security primarily depends on three key factors. First, the people; second, the processes; and lastly, technology. For this reason, you’ll see the ‘People Security’ area at the bottom right of our diagram.
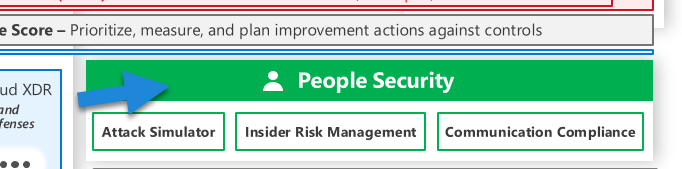
The People Security area in the diagram reflects an essential truth in cybersecurity, that human behavior and actions significantly impact the security posture of an organization. Essentially, this area focuses on the security aspects related to the people in an organization and their interactions with systems and data.
The signals are evaluated by three main azure Security features:
- Attack Simulator: This is a tool found within the Microsoft 365 security center. The Attack Simulator allows security teams to simulate various types of cyberattacks in their environment without causing any harm. This helps them understand potential vulnerabilities in their human and system defenses. For instance, you can simulate phishing attacks, password spray attacks, and brute force attacks to test your organization’s resistance to such threats. The outcomes of these simulations can help educate employees about the risks and proper actions to take when faced with real attacks.
- Insider Risk Management: This is a solution in Microsoft 365 that enables organizations to detect, investigate, and act on malicious and inadvertent activities in their organization. It uses machine learning algorithms to identify risky activities such as data leaks, data theft, and violation of policies. Insider Risk Management is a crucial aspect of ‘People Security’ because it acknowledges that threats can come from within an organization, not just from external actors. By proactively managing and mitigating insider risks, organizations can prevent significant damage.
- Communication Compliance: This feature of Microsoft 365 helps minimize communication risks by helping you detect, capture, and act on inappropriate messages in your organization. It helps ensure that communications in your organization comply with internal policies and external regulations. It can analyze text and images across Microsoft Teams, Exchange email, and third-party communications platforms. Communication Compliance is important in maintaining a safe, respectful, and compliant workplace environment.
These three aspects together help organizations simulate potential attacks, manage insider risks, and maintain compliance in communications, providing a comprehensive approach to managing people-related security risks.
Data
The Data area holds a paramount position within the Azure security framework, simply because everything depends on data. The first line of defense is Azure Purview, which discovers, classifies, and labels data. The generated labels are then utilized by Azure Information Protection, adding another layer of protection to the data that has been classified.
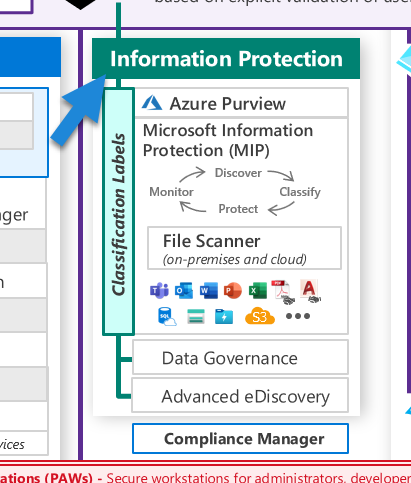
Azure Information Protection not only safeguards the data but also offers valuable advice and recommendations about data protection. It helps to maintain the confidentiality and integrity of sensitive data, such as personally identifiable information or proprietary business information, by ensuring that it is appropriately classified and protected according to its level of sensitivity.
Backup forms a crucial part of data security. Azure Backup provides features to secure this essential asset by implementing strict access controls, like PIN verification and multi-user authorization. These measures require that another person authorizes the access to a backup, thereby adding an extra level of security. This multi-user authorization approach helps ensure that backup data cannot be accessed or modified without the consent of multiple authorized users, thus reducing the risk of unauthorized data access or loss.
Ultimately, the data component of the Azure security landscape is designed to ensure that data is not only stored securely but also used and shared responsibly, maintaining its confidentiality, integrity, and availability at all times.
SIEM/SOAR
SIEM/SOAR (Security Information Event Manager / Security Orchestration Automation Response) stands as a significant layer in the Azure security structure, providing a high level of alert management and security response automation.
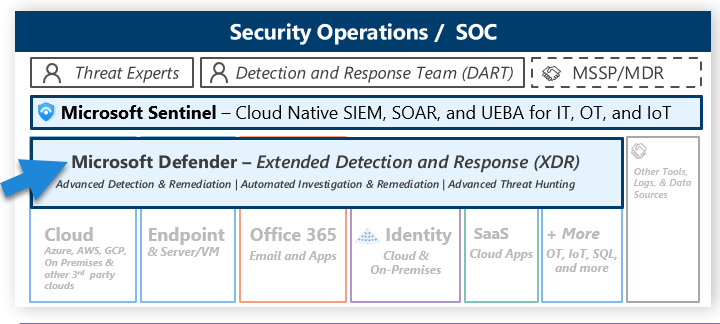
Azure Sentinel, Azure’s cloud-native SIEM/SOAR solution, sits atop the Log Analytics workspace, which is a cloud-based data collection, storage, and analysis service. It uses connectors to collect data from various sources, ranging from Azure resources to on-premises systems and security solutions from various vendors. This data is then used for threat detection, investigation, and response.
Azure Sentinel harnesses the power of the Kusto Query Language (KQL) to perform several key functions:
- Threat Detection: Sentinel uses KQL queries to analyze the collected data for possible threats, identifying potential security issues within the infrastructure.
- Threat Hunting: Sentinel takes a proactive approach to security, using KQL to search for potential issues and anomalies that might indicate a security threat. This can help identify issues before they become major problems.
- Threat Intelligence: Azure Sentinel’s use of KQL goes beyond simple detection and hunting. It can perform complex analysis to detect advanced threats and potential attack scenarios, leveraging threat intelligence feeds and other sources of information to provide deeper context to the security data.
- Incident Response: Azure Sentinel can automate responses to security incidents using playbooks and Logic Apps. When an incident is detected, Sentinel can automatically trigger actions like sending emails or initiating other processes to mitigate the incident. This capability falls under the SOAR aspect of Sentinel and can greatly reduce the time it takes to respond to an incident.
In essence, Azure Sentinel provides a robust, automated solution for managing security data, detecting and responding to threats, and automating routine tasks. This makes it a key component of any comprehensive Azure security strategy.
You’ve just journeyed through the robust world of Azure Security, breaking down complex concepts into bite-sized insights. Azure Security isn’t just about firewalls and encryption; it’s a dynamic ecosystem that encompasses Endpoint Security, Network Security, Infrastructure Security, Signal collection, Data Security, SIEM/SOAR, and People Security.
You’ve seen how Azure’s security services are intricately linked and how they rely heavily on policies to maintain a unified security front. You’ve seen the importance of your network, which forms the backbone of your security, and how Microsoft Defender keeps an eye on everything from IoT devices to Containers.
Remember, like most journeys, understanding Azure Security isn’t a one-time event but rather an ongoing process. As Azure continues to evolve, so too will the security measures needed to protect your data and infrastructure. But with this solid foundation, you’re well-prepared to stay ahead of the curve.
In the end, it’s about realizing the potential and embracing the power that Azure brings to your organization’s security posture. With Azure Security, your organization isn’t just surviving; it’s thriving, unleashing new potentials and possibilities.
Thanks for joining me on this journey, and here’s to your continued success with Azure Security!

