I decided to write a short article about this important topic because I am discovering some very nasty techniques to hack into Microsoft Azure environment.
From my studies, at the moment, the most dangerous and easier attack is the privilege escalation, and this is for many reasons.
People don’t look at the accounts and the passwords, and they underestimate the attack surface, company look at the cloud as a unique agglomerate of technologies working together in a separate network isolated from the world, but this is entirely wrong.

In this world everything and anything is interconnected, we are an extension of the cloud, it can be Azure, AWS or Google, there are no differences between them.
We connect to the cloud in many ways, using a web portal, scripts, software and tools, we cannot use the cloud without connecting to it.
We decide to use the cloud, we ask for a service, the cloud provider or our cloud administrator will grant us an authentication to the service, and he will also provide the necessary authorizations to use the service.
Authentication and authorization are the two main pillars in the security, and a privilege escalation attack also has two phases, first, it finds a way to authenticate and after it escalates in the environment to get more authorization as possible.
How is a hacker able to find a breach in our cloud?
The question itself is misleading because the hacker doesn’t look in the cloud; he looks at the user; we are the real objective of the hacker.
We can close any door in the cloud, but we also need people able to enter in these doors to support the infrastructures, to use the services and more, we cannot use the cloud without connecting to it.
The cloud providers are investing a lot in the security space, creating and inventing any new way to protect the user. Still, there is always the human factor to consider, we are the real problem, often due to our lack of responsibility.

Microsoft introduced MFA , multi factor authentication, which is a great feature, unfortunately not many people are using it, from the BlackHat conference Microsoft announced that at 2019 only the 8% of companies used MFA.
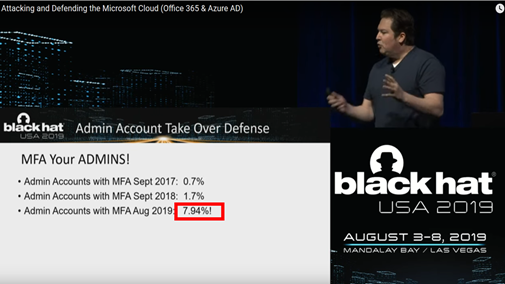
Also using MFA you can be at risk of attack, it depends by the settings you use, for example, we provide to the users the possibility to use the check to avoid the MFA for 14 days.
I found some critical exploits in authentication mechanism in Azure, and I developed some scripts able to exploit credentials and authentication from a computer.
The way to perform this exploit is not necessarily complicated and the requirement is one only, the code must be running in the machine.
There are many ways to execute a script or code in a computer, remotely, using a USB Rubber Ducky, physically accessing in the computer and more.
The most crucial point is one, it is relatively easy to still the credentials, access into the cloud and create a backdoor.
I am an ethical hacker, and I am not going to explain in public how I have been able to do that, but I can show the output.
The script first looks for the exploit in the machine.
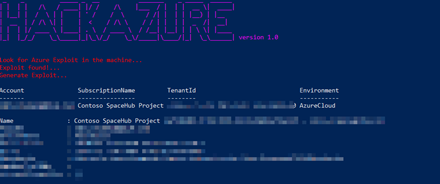
When found it then it will try to create the backdoor, which is actually a Service Principal account.
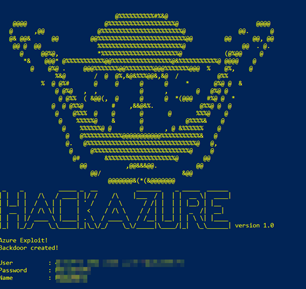
The most preferred victims are IT Administrators, and a good strategy for the hacker is using social engineering to identify the IT Administrators in the company.
After that, he can approach him in different ways, by email, creating friendship, another frequent technique is hiring.
It is straightforward for the hacker to get hired by the company, they prefer low-level profiles like the developer of Junior administrator, and they approach the target in without any problem.
For all these reasons, the best approach to use in security is the Zero Trust, never trust anyone, provide less credential as possible, remove access to any sensitive information, especially from internal.
It is very natural for the company to block access from the external, but what about the internal?
An example is something that happened to me time ago, I was discussing the importance of limiting the Global Admins account from Azure.
This administrator told me, “Nino I know all these people very well and we can trust them”, this is when the problem may happen, when we start trusting users, this is what I mean for Zero Trust.
I implemented some security scenarios, and I am planning to create some webcasts, and I also have in plan some conferences in the next months, and I will show in real these attacks.
I tested many scenarios and even using MFA, we can be vulnerable, unless we force the authentication every time the user logs into Azure; unfortunately, this is not a normal practice.
Another great defence is AMI, Azure Managed Identity, using AMI we can remove any type of authentication across the users and systems.
We have two types of AMI, System and User assigned and the main difference is one, the System is managed by the resource itself, and we cannot share the identity across multiple resources,
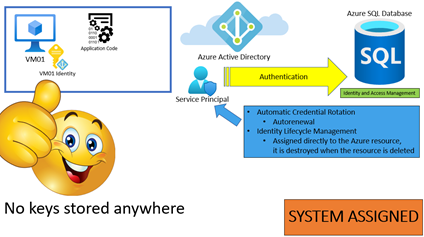
and the User one is governed by the administrator and shareable across various Azure resources.
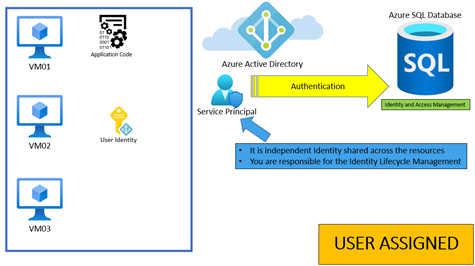
The basic principle behind that is elementary and the same in both cases, the Azure resource use a principal service account to authenticate to the Azure resource of destination.
There is one case only where AMI uses an Azure Key Vault and key, and this is the case if we need to integrate into an on-premise environment.
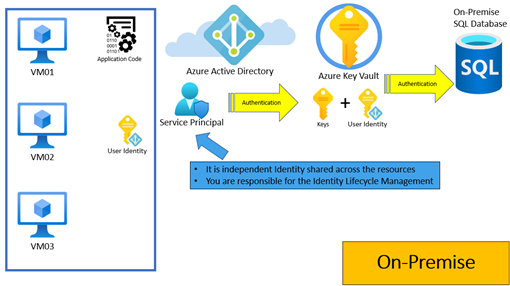
Not all the Azure resources can use AMI, and you can find a full list below.
In conclusion, don’t trust anyone, remove any access to any sensitive information in the cloud using AMI and force your user on using MFA withing force authentication.
If you want to know more about that, join me in my sessions and feel free to contact me for any more information.

