The scope of this article is to provide a good understanding and vision of cloud security. My willingness is to share my experience and provide very useful insights to people working in key company areas like Sales, Managers, High Stakeholders. I recommend the reading also to technical people, like security roles, developers and IT administrators.
Security is a huge wide-open topic, and in this article, I will refer to cloud security and to Microsoft Azure as platform; however, the concepts contained in this article are applicable to any cloud platform.
Preface
I started my career when the internet was populated by BBS, and a 2400 modem baud speed was considered a privilege. I started looking about hacking the first moment I installed my first MSDOS operating system on a computer. That was actually my brother’s computer, and my parents gave it to him for his birthday, it was abandoned in a corner. The computer was a Compaq Deskpro; I was reading the computer manuals, and I was looking to understand how computers work. I understood about computer interrupts the famous INT 21, the memory registry, how the operating system was using these interrupts to manage hardware and programs in memory. For those who are not familiar with these concepts, and the operating system uses interrupts to manage almost everything in the computer, to shut down the computer, to write data on disk, To switch a led on. For example, when your DVD write software opens your DVD to require the disc, it actually set some registry to define the operation Open DVD door and invokes a specific interrupt number.
Without being too much technical, this is also why during a high CPU percentage in System Interrupts, and you see the computer almost getting stuck; this usually happens when the operating system is struggling to manage this essential and vital area.
Back on my story, I was reading about the debug.exe MSDOS command, and I learned about the possibility to disassemble and executable, I was actually able to read how an executable was executing interrupts and setting registries in memory.
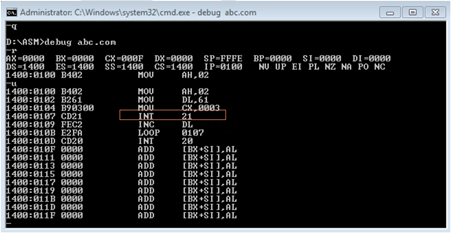
I noticed a recurrent NOP symbol. I learned that NOP is a no-op, no operation instruction, the NOP instruction means do-nothing, like a null space in memory. I noticed that sometimes these NOPs were many, and all together, creating free space in the program. I started thinking, is this maybe a space I can use? What will happen if I can write interrupt commands in this space. I investigated more in the debug command, and I found the command to write and reassemble the executable. I looked for the registries and interrupts to open the CD reader, and I wrote these sequences in a game program. I think it was the first version of GTA. I reassembled the executable, and I executed the game, and BAM!, the game started, and the CD opened the door, my mind blew up!
What I just described is a buffer overflow attack. I was not aware of this, but I actually conducted a buffer overflow attack, all by myself, without reading anything around, I didn’t even know about hacking or hackers or what exactly a computer was.
This is how this happens, and this is how a hacker thinks, how he operates. It is so fascinating how we can see and find ways to manipulate our reality around us in a way that nobody was thinking about before.
This is how a hacker finds vulnerabilities and ways to exploit technology, and the same process works with any type of technology. The technology evolves, but the concept is always the same. Operating systems are still using interrupts, and companies use specific scanners to scan their code to avoid this type of attack in the application, but this type of attack is still very possible.
Introduction
Let start with the important and basic concepts, offensive and defensive security, white and black hat hackers, and at the end, the cybercriminals.
Offensive security is the area that covers attacks to the systems, and it is focused on attacking a target; the target can be a system or a physical premise, and try to exploit any vulnerability using any possible way and tool.
Defensive security is the area that covers the defence of security, it is focused on defending the target, and the target can be a system or a physical premise.

White and black hackers have exactly the same offence abilities; white hackers are usually ex black hackers, and sometimes, vice versa.
The white-hat hacker conducts offensive and defensive security to stop and prevent cyber-attacks. They work under a contract and with the permission of the target.
The black hat hacker conducts offensive security only. They work independently, and without the permission of the target, sometimes they operate for good. For example, many months ago, a large criminal online organization was blocked thanks to a black hackers group, they hacked the criminal organization servers on the dark web, and they shared all the information to the FBI and newspapers.
The cybercriminal conducts criminal activities using technologies, they are often addressed as hackers by the public, but these are not hackers. These people are just criminals.
Security is such a wide-open topic; any actor in the company looks at security in a different way and perspective, business, infrastructure, strategy, technical and more. I want now to discuss my point of view about security for the most important key company areas.
Security for the salesperson, and not just salesperson…

I recommend this reading to everybody, and I think it contains very interesting resources for any role and profile.
Security can be a very good market spot, a lot of security companies are able to generate massive revenues, and there are many types of projects and activities that can be proposed. Even more, wide-open generic consulting companies can generate interesting revenues from security. Let give some examples. A security and compliance assessment in a medium cloud environment can take between six months to one year. Security is also a great opening door, and it is a great opportunity to start an interesting conversation, engaging some very short time specialized activities able to build a very good trust relationship with the customer.
In my opinion, security can be a powerful weapon for a salesperson because any company is interested in being more secure and safe, but it can also be a very dangerous topic to discuss. Nobody likes to admit that there have security weaknesses in the company or that good security practices are not well implemented. For that reason, starting a discussion around security and asking the wrong questions could be more harmful than advantageous.
Where to start?
It is important to build a solid base, and a salesperson doesn’t need specific technical expertise. He needs more a good understanding of security from a business and strategy perspective. This is also a good vision to have for managers and high stakeholders. There is a lot of material on the internet, and Microsoft provides
Microsoft Cloud Adoption Framework for Azure is a perfect spot to start, and it contains a lot of material and resources. The Microsoft CAF contains documentation and guidance to help companies in the cloud adoption journey.
https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/
I selected these specific readings that I consider the most important articles to read.
This article provides a clear understanding of Security Strategy, and the strategy is an essential topic to understand first.
https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/strategy/define-security-strategy
The article below provides a clear vision about company roles and functions
https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/organize/cloud-security
This article explains how a company should manage security
https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/get-started/security
The article below provides an essential list of the most important security practices
https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/secure/security-top-10
A good business opportunity is the Microsoft Solution Assessment Program. In this program, Microsoft provides many interesting incentives for partners.
This is a short video recap https://www.microsoft.com/en-us/videoplayer/embed/RE4DaNa
Microsoft well architected Framework, the security area, is another great resource for a salesperson who likes to get a bit more into the security without being too much technical. There are several interesting videos explaining the most important security
Material and templates
Microsoft is providing useful material to start, like PowerPoint templates, questionaries and more. I collected what Microsoft Microsoft Cloud Adoption Framework for Azure is providing in this zip file that you can download here
The package contains very useful material, below and example of email template you will find in this package.
The package also contains a questionnaire to use during a workshop:
There is a PowerPoint slides template:

This is all free material to use, and I think it can be very valuable to use.
Security for Managers and high stakeholders
This section is more specific for managers and high stakeholders; however, I recommend the reading to anyone.
For about five years of my life, I led a global Azure cloud infrastructure for a global manufacturing company. I was reporting directly to the CIO, my role covered any area, from strategies to infrastructure, also working with teams in hands-on technical jobs, organizing teams, and my priority was providing guidance and rules to the company to achieve solid cloud governance and security. In that period, I built a huge amount of experience, I made many mistakes, and I learned a lot from them.

Managers and high stakeholders are the most important and strategic people for security, even more, important than the SOC team or IT Security operators. I have been invited to several security roundtables to discuss many security topics, and I had the opportunity to listen to many different opinions and real experience stories from other people like CTOs, CIOs, Managers, and more. In general, we all agree about the importance to push proper security awareness and practices in the company; something I noticed in my past experiences is that companies are starting to be very aware of security when something bad happens. The problem is that the bad has already happened.
Security threat is often related to software and infrastructure. For that reason, companies look at software development and infrastructure as an important and critical area. In my opinion, managers and high stakeholders are the most crucial area, and I think that culture and discipline must come from the top.
Companies create initiatives like the Security Champion to connect developers with security people, and this is great, but this is focused on the lower layer of the process. Developers are focused on developing source code, and they are often under delivery pressure from the top management. Usually, the management is more focused on the budget and production optimization than security, and we cannot rely on a developer to explain to a manager how much is important to write secure code.

It is crucial to use a proper strategy, and in my opinion, it is a top-down responsibility process. It is like that we are pretending to have a good child coming from a mum who doesn’t care at all about his education. Does it make sense?
The management layer is responsible for driving the company, and they need to push the discipline and practice as a very first example. A great pattern to use is listing all security threats and risks at first. It can be in the case of a project, or an initiative, or any type of activity. For example, during the project analysis, we evaluate and list all possible security threats and risks. This is extremely useful for many reasons, and the most important is that managers and architects are aware of these security issues. They know that these are security threats must be addressed. Using this pattern, it is going to be much easier to plan a great security practice during the project, and more importantly, the management is aware of these risks, and they need to get the responsibility for them. I think that it is wrong for a manager to rely on developers and security tools for security, I think a good manager must be the first person responsible for pushing security awareness in the company.
I met many companies using Microsoft Azure without knowing what a Cloud Security Policy document defined, or not even a cloud incident management process document. The first thing a CIO must have is a cloud security policy document to define the company rules for the cloud. These rules must be approved by him first and pushed in the cloud infrastructure enforcing policies. All the companies policies must be enforced in the processes using proper tools. This is what I define as Corporate Policy.

We will speak later about this important aspect which includes the strategy, but how does an Azure Policy Document look like?
The document must list all the important areas, like Tenant, cloud resources like virtual machines, storage accounts, and important areas like network and data. For each area, we list the policies we want to enforce in the company and that users must respect.
I want to give you a very practical example of policies:
- Multifactor Authentication must be enabled in all accounts.
- Public port RDP (3389), SSH (22) and Telnet (23) are not permitted, no exceptions.
- Antivirus must be installed in the Virtual Machine.
- Just in time, access must be enabled. Just-in-time (JIT) virtual machine (VM) access it is used to lock down inbound traffic to your Azure VMs, reducing exposure to attacks while providing easy access to connect to VMs when needed.
https://docs.microsoft.com/en-us/azure/security-center/security-center-just-in-time - Endpoint protection is set to on for VM exposed on the internet, and it is also recommended for the internal endpoints.
https://docs.microsoft.com/en-us/azure/security-center/security-center-endpoint-protection - Operating System Vulnerability recommendation policy must be enabled.
This policy daily scans the VM for possible vulnerabilities. - Enable Microsoft Monitoring Agent for any critical VM on the frontend. Backend VM will be evaluated in relation to the scope.
- Integration Under Threat protection must be enabled for any critical and frontend VM.
- Multi-Factor Authentication must be enabled for any domain user that has access to the VM.
The cloud policy document is a very interesting topic, and I will explain a cloud policy document in a next article.
When the document has been approved and signed, we enforce these policies in the company. What exactly means enforcing the policies?
Depending on the area, we use the proper tools and practices. For example, in the cloud, we ask the IT administrator to enforce the policies using Azure Policies, we ask the project managers to enforce the proper security tools in the developer tools. Essentially, we put into practice what we defined in the Azure policy document.
A fantastic resource to better understand policies is this video from my colleague Microsoft MVP
Adam Marczak
Another important point to look at for managers is the security and cloud strategy. Without a clear strategy, it is just a journey into the unknown.
I want to recommend you something to read and be able to provide you with a good understanding.
The Microsoft Cloud Adoption Framework for Azure provides one specific area dedicated to the strategy, and it defines four important stages.
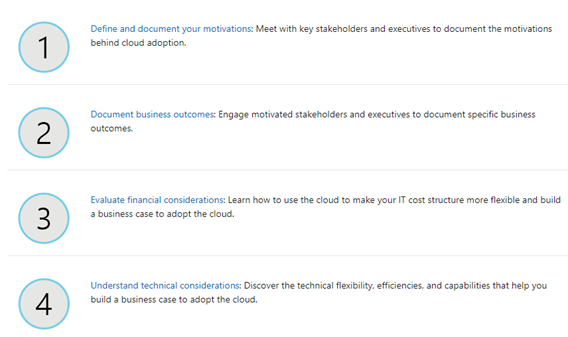
I recommend you the reading about the Strategy, the documentation often refers to migration and innovation. I recommend you to read these resources in a very pragmatic way. Consider yourself as a company looking to migrate into the cloud, even if you are already in the cloud. Think about your real motivations and targets.
The second reading I recommend is the Governance in the Microsoft Cloud Adoption Framework for Azure. The methodology article is very useful, especially the recommended reading.
Another very useful resource is the Cloud Adoption Framework Governance Benchmark Tool. This is an assessment to identify gaps across key domains.
Conclusions
Security is such a complex topic, I hope that I have been able to provide you with some interesting insights from my personal experience.
I hope you enjoyed this reading.

