In my last post, we discussed the importance of understanding security first. Today I would like to discuss something that I consider the real principle of security, the main and most important law.
The first law in nature is, “Nothing is created, nothing is destroyed, but everything is transformed”, following this very important law we are able to deeply understand how nature works.
The first law in Security is, “Security transcends Technology”, this law is at the base of the entire security spectrum. In security the order we need to follow is always the same, in any problem or situation, people first, process second, and the very last technology.
From this principle, we are now at our second tip, “The success of the technology depends on the people and the process first.”
I see companies and people speaking about technology as a solution to protect the company and solutions from any type of attack, but the question in my mind is always the same, how can they know, if a specific piece of software, is what they need to solve the problem without having a clear idea about what exactly is the problem to solve?
We can use any security technology we want but, for instance, if our people are not configuring the environment correctly, our effort is completely useless. We can use any source code scanner we want, but if our developers are not aware of how dangerous can be to save company information and configuration in their laptops, there is nothing we can do to avoid very dangerous attacks.
The same is for the process level, anything in our process must be secure, and we need to use the correct security technology to make it secure.
People are the most dangerous and vulnerable target, yes exactly, I said also dangerous.
I want to give you a very interesting experiment to conduct, which will be able to really understand this concept.
I invented this experiment to understand how much humans perceive security, I called this experiment, “The chaos monkey experiment”.
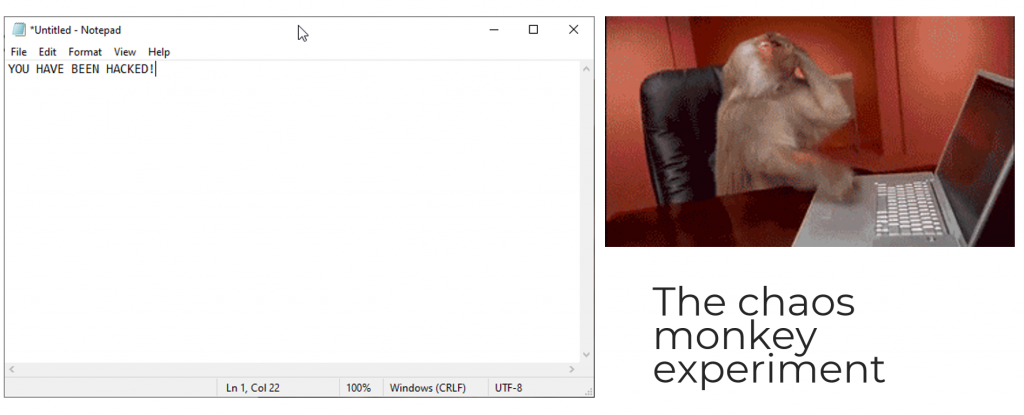
This is how the experiment works.
We often see people leaving the desk without locking the computer and leaving the account session open, and we know this is wrong, but we are human.
Next time you see that, go to the computer of your colleague and open a notepad, and write this sentence on the notepad, YOU HAVE BEEN HACKED!, go back to your desk, wait, and see what happens.
You will be amazed by the reactions you will see, and it will give you a completely different vision of security.
Most people sit and look at the screen for a minute, they look left and right, quiet, and they start thinking, maybe it is a joke, or maybe I have been hacked for real, so what to do now?
There are two options only, the first option, you ask people who made this joke and hope that someone really did that, or, the second option, you write an email to the IT Security Admin and tell him that there is a possibility you have been hacked.
The psychological and tragic issue here is that, in both cases, you need to admit that you have done something terribly wrong.
In most cases, after a minute of total panic, the person closes the notepad and keeps working as nothing happen.
This is the biggest problem in security, humans are not designed for security, and we need to teach and educate them about security.
People are always the first layer in security, if your people are not on board with security, then there is no way you can make your company secure, and this starts from the very top, the high stakeholders. The high management pushes the culture in the company, if management does not care about security, the entire company is not secure, at any layer, and this is a must.
When I do security assessments, the first thing I do is speak with high stakeholders, this is giving me a quick understanding of security across the company.
I will speak about the management and high stakeholders in another specific tip for them, for the moment let’s keep the discussion higher.
After people we have processes, anything we do in a company is governed by processes, if our processes are not following correct rules and policies, we cannot be secure, no doubt, even if we use the top security technology in the world.
Let’s speak about SolarWinds, a multimillion software company, with top-level security policies, and a software administration platform used by the entire world, despite all this, they have been brutally hacked in the core.
How SolarWinds attack happened?
I don’t want to dig into the very fascinating history of this, which would push back us to 2014, when the real cyber warfare started, if you like to know more about that, I recommend to you this amazing and unique book, “This Is How They Tell Me the World Ends: The Cyber Weapons”

If you like to really understand our world from a cyber security point of view, then this is the book you need to read, you can find the book here.
But let’s stay on the real point of this type of attack, a piece of code able to open a reverse shell communication has been injected into the SolarWinds delivery pipeline.
The day SolarWind released the path, all companies using the software have been exploited.
The truth is that the attack has been discovered after a very long time, and during this time the attackers had full access to almost any major companies and organization infrastructures in the world, even Pentagon and NSA have been exploited.
We don’t know how much the attackers have done during this time, this is in my opinion the most devastating cyber attack in history, and I think this was just the start.
My point here is that, if a company like SolarWinds failed in its security-delivering process, then think about how much can be dangerous to underestimate a possible attack on your processes.
Code injection in delivering pipelines is for sure one of the most preferable ways to attack, it is stealthy and able to provide a very large attack surface, and most important, it provides the best way to execute the attack in signed code and usually in the higher privileged account.
There are many other things to consider in such a critical situation, like the legal one, where the concepts of Due Diligence and Due Care become the real key points to save our company, but this is another article.
In the next article, we will explore more the technology side, something more into the dark side of security.

