Sync and Federation between Microsoft and Google, How to, What it is important to know and Why.
We are living in a multi-cloud culture, and integration across different cloud providers is now a must. In these days, I looked at the integration between Microsoft Azure and Google, and I want to highlight the most important information we need to better achieve that, the pros, and cons and how to plan this. I hope to provide you with good reading, enjoy.
The scenario:
Contoso is a multi-cloud company using Microsoft Azure, Google Cloud, Microsoft Office 365, Google Suite, and many Microsoft Dynamic 365 products. The CIO is looking to integrate all these technologies usability without compromising productivity and without affecting the user experience.
Now
Contoso uses several technologies like Microsoft Office 365, Azure Portal, Dynamics 365 products, Google Workspace, and it uses different domains, one for the Microsoft side and another for the Google one.
Next
Contoso wants to centralise the authentication across all collaboration tools in the company, which means Microsoft Office 365, Azure Portal, Dynamics 365 products, Google Workspace under a unique domain named azureofficesuite.com.
Why
Companies use many of the great features and product offered by Microsoft and Google. Both the company works together to provide the best experience in term of integration and cross-usability. Microsoft Office 365 is a very well-known collaboration platform with Teams and many other powerful stacks as Power Apps and more.

Dynamics 365 provides a large number of well-known valuable business products, and Microsoft Azure is a point of reference for cloud computing.
Google is also offering many interesting collaboration products in the G-Suite

Google Cloud also offer a cloud computing experience with many products and options. We are living in a fast world, where new technologies come up every single day and offer interesting new features and opportunities for a new type of business. We need to rely on each other, and we need to work all together in the interest of our future. People and companies are using everything in the market space. People and companies want integration. The business today is integration.
Microsoft and Google work closely to provide integration across their platform because this is in the interest of everybody.
What it is important to know and understand first
Azure Active Directory (AAD) is a cloud service offered by Microsoft to manage user identity in the cloud. All Microsoft cloud services depend on AAD for authentication, with also means Microsoft 365, Office 365 and of course, all Microsoft Dynamics 365 products. The same thing works in the Google Workspace and G-Suite. What I want to highlight here is that to provide access to your accounts into Dynamics and Office 365 products, you need to have an account in Microsoft 365 (M365), and M365 directory accounts are an extension of AAD.
We work with Azure AD and Google Workspace, and we will connect to integrate them, more specifically on the Microsoft side.
Another important takeaway I have got from this exercise is that we need to work with very crucial domain settings and certification across both providers. I recommend doing this operation using a test environment first and repeating the same operation a second time in production. The risk I faced was to lose the possibility to use the google accounts for some hours.
Google suite has the concept of primary and secondary domains, and the primary domain is considered the key point for any integration and usability. In Google Suite, we can create our own domain hosted in Google or attach an external domain, the external domains hosted by external providers are more configurable. Google doesn’t permit changes in some of the DNS settings for a primary domain hosted in Google. We also need to consider that if something wrong happens to the primary domain, we may lose the possibility to log into G-Suite again. It is important to have a backup plan, like a main secondary user.
In the case of a large environment, I recommend coordinating the support with Microsoft and Google before starting.
How to
We have now a clear understanding of the scenario and challenges. Let dig into the more practical side, how to do that.
Register the domain in M365 and create a test account
The first operation is to register our domain in Microsoft 365 (M365).
Enter in https://admin.microsoft.com
Select Settings > Domains
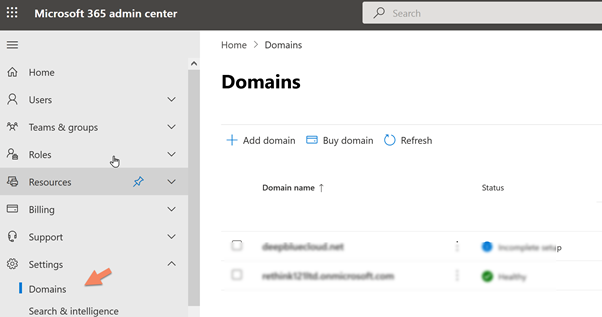
Click Add domain, and we register the domain using the simple wizard process.
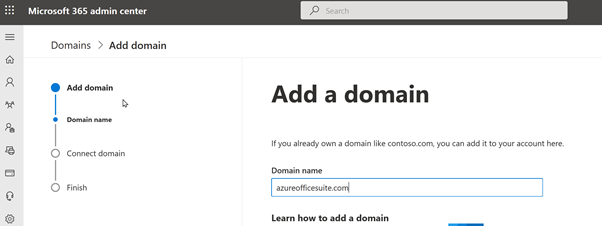
We can refer to the documentation below for any additional troubleshooting
https://docs.microsoft.com/en-us/microsoft-365/admin/setup/add-domain?view=o365-worldwide
Configure the Domain in Google Workspace and create a test account
We now need to set the domain in Google Workspace.
Navigate to https://admin.google.com/ac/domains/manage
Select Domain and Manage Domain.
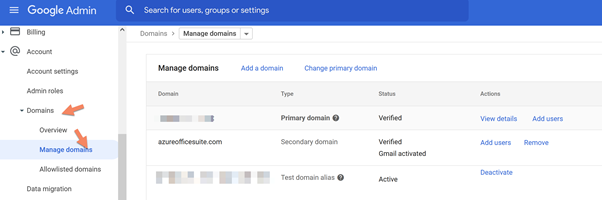
Enter the domain name and set a secondary domain
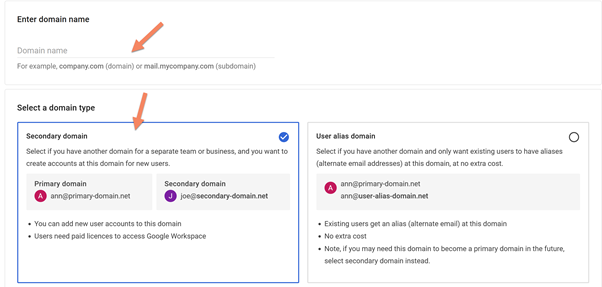
Follow the next simple steps to register the domain.
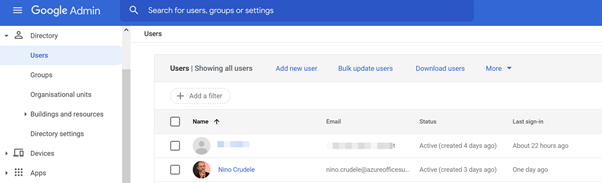
Now go in directory Users and create the same user as we did in Azure AD
A great feature is Auto Provisioning, and this is something we can enable in Azure AD when everything is set. Auto-Provisioning provides the possibility to synchronise the accounts from Azure AD to Google Workspace.
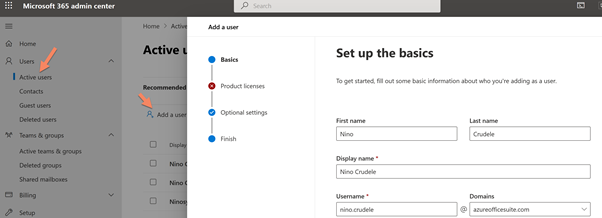
For now, we will manually create a test user to use for testing purposes, and we will need to create the same user on the Google Workspace side.
Select users and active users and click add users, set the user email and the domain to sync; in my case, I used my name.
Configure Azure AD
To use a single authentication account across different domains and using a single one, we need to use a Single sign-on (SSO)
SSO requires a unique point of reference to sign the user across the different platforms; for that reason, we need to provide a single login page. Microsoft Active Directory provides this feature.
Enter in https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/LoginTenantBranding
Select Azure AD and click on Company Branding
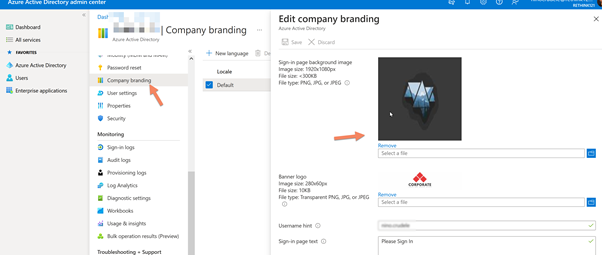
Set the background, logos and any relevant information we like to show on our login page.
We can refer to the documentation below for any additional troubleshooting
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/customize-branding
Register the G-Suite application in Azure AD
Microsoft Azure uses the concept of Enterprise Application to handle the application in the cloud, which means monitoring, managing, creating and configuring. For that reason, we now need to configure the Google Workspace application to start this integration process.
This is one of the most important steps.
Enter in Azure AD and select Azure Active Directory.
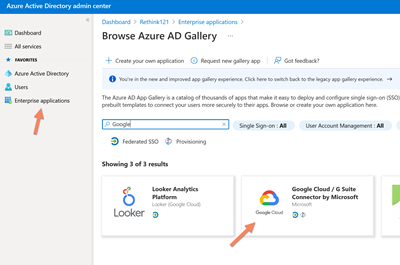
Select Enterprise Application, click on New Application and search for Google.
Select Google Cloud / G Suite Connector by Microsoft.
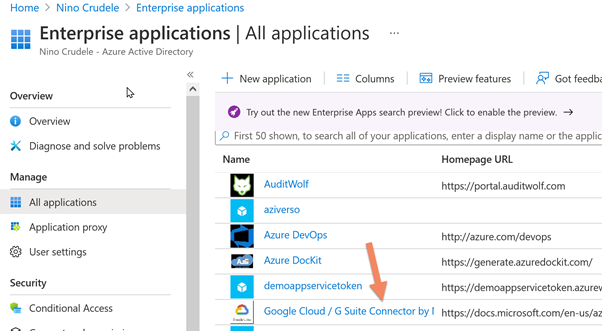
After installing it, select the Google Cloud / G Suite Connector by Microsoft in Enterprise Applications
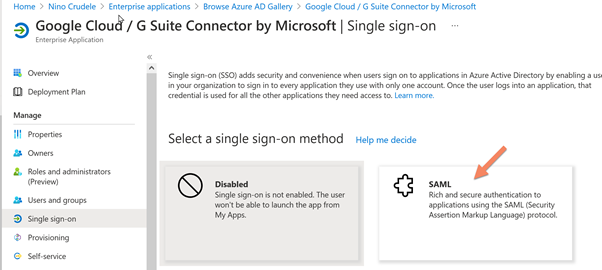
Select Single sign-on and click on SAML
Click on Edit
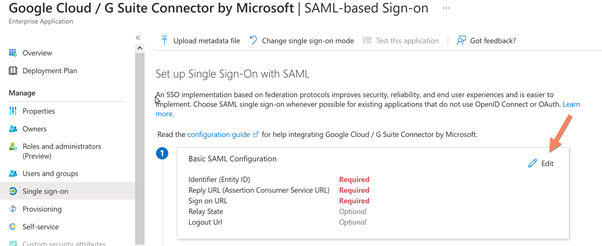
Below the settings is the Identifier Entity ID. These entities are used during the authentication process by both domains. The Microsoft Domain will become a SAML token to Google Workspace, which will reply with an Entity ID. In the case of Google, the first exchange will use the primary domain in the SAML token. This is the reason why it is important to specify it and set it as default.
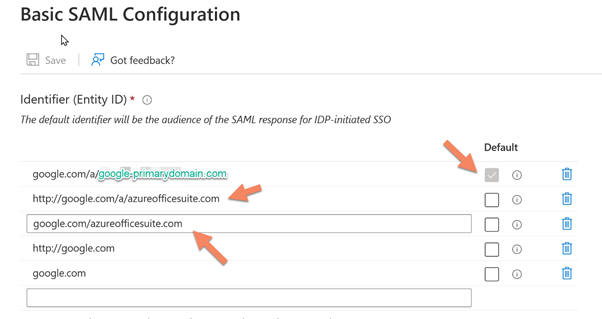
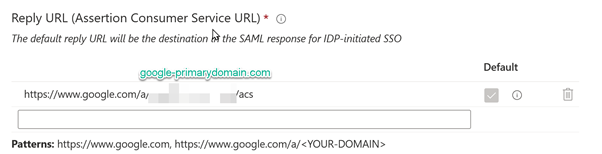
The reply token from Google will also require the primary domain. An important note, you can see below that the reply I set is not corresponding to the pattern suggested by the tool. During my tests, I faced some errors, and I discovered that the value set in the SAML token was different from what was suggested in the documentation.
You can see that in my setting, there is a /a/googleprymarydomain.com/acs
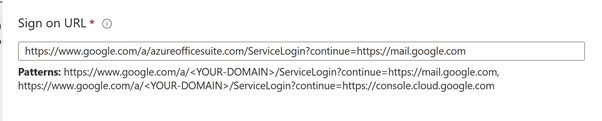
And we set the Login page
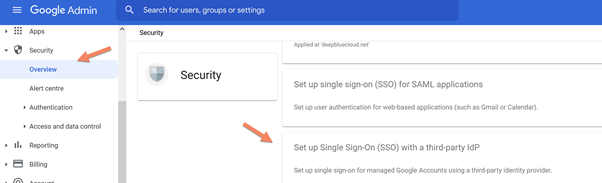
Configure Google Workspace
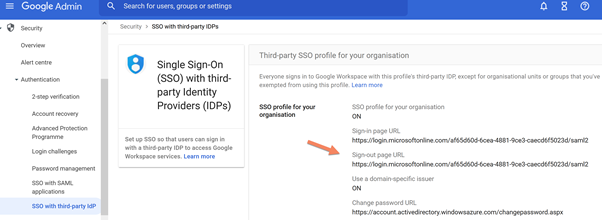
Enter in the Google Workspace and click on Security and click on Single Sign-On (SSO) with third-party Identity Providers (IDPs).
Set all the values following the specification below, and you can find all the values to use in the Azure AD; also download the raw certificate to use in Google Workspace, below the Azure AD side.
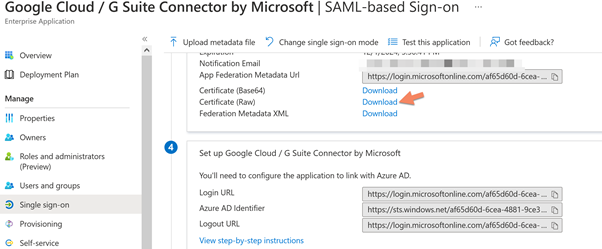
Below you can see the Google workspace side and the value set.
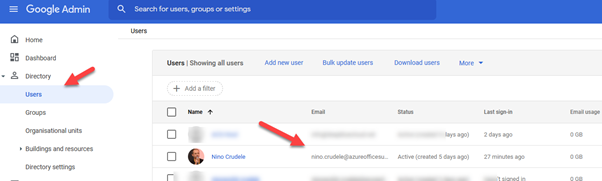
Create the user in Google Workspace
Select Directory and Users, and add a new user with the same name and domain as Azure AD
Test the integration and troubleshooting
We can test the integration by clicking on Test this application, and we can find this in the Single sign-on setting of the G-Suite application in Azure AD.
We cannot use any browser because it requires an extension; I recommend Goggle Chrome.
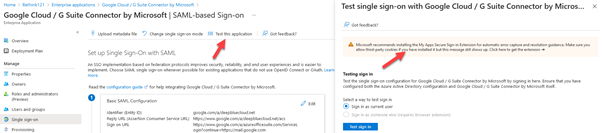
To get the best result, I recommend testing the integration using the account we created; in case of error, past the error in the box “What does the error look like?” and click Get resolution guidance.
An important thing provided by the extension is the possibility to download the SAML token; in this way, we can investigate the response.
Another important tool to troubleshoot this integration is Wireshark, and you will need to install the certificate to decrypt the transmission.
Select Sign in as someone else (requires browser extension) and click the test button.
Here starts the magic.
We now see our new login page with our company logo
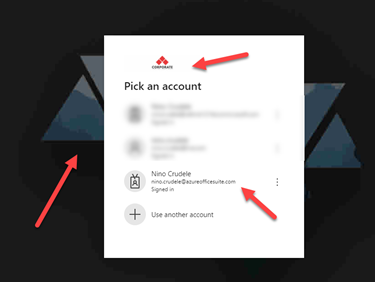
Proceed with the test, and you should have the result as below.
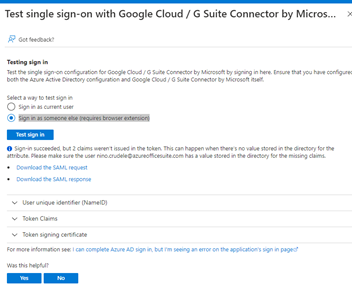
I recommend you download the SAML request and response, and this is a great opportunity to better understand the handshake between the directories.
Azure AD Auto Provisioning
The last thing I would like to leave you with is auto-provisioning. Azure AD provides the possibility to manage all users between Azure AD and Google Workspace from the Azure AD console. It is important to highlight that this mechanism works in two ways, from Azure AD to Google Workspace and Vice versa, depending on if we use the manual or the automatic way.
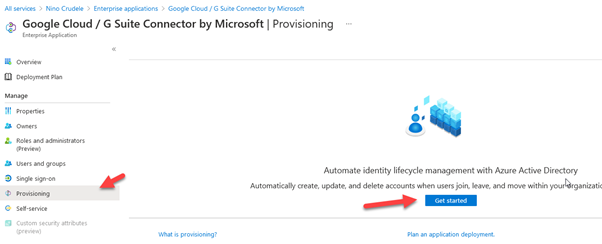
To enable the auto-provisioning, we need to navigate in the G-Suite enterprise application in Azure AD and select provision.
Conclusions
The collaboration and integration across Microsoft and Goggle can offer a lot of advantages, I hope you enjoyed the reading and you found this article useful.

