We use AES encryption and hash algorithm every day in Azure but sometimes we misunderstand the differences between them and the using.
Azure uses encryption and hash everywhere, for VPN, to encrypt databases, passwords, to secure protocol and a lot more, so it is very important to understand where and when we need to use one or the other, the user of Azure Key Vault is a good example.
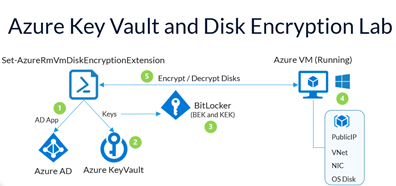
Without a clear idea about these topics we may occur in the risk of a security weakness or we are not able to understand if the solution that people are proposing us is correct, so let have a look into it.
This article will provide you some basics but a very clear and useful understanding about these two important topics.
We use encryption every day in many situations, and it is very important to understand where we use these types of encryption because the using of a wrong type can compromise security, performances and reliability.
There are two basic type of encryption, Asymmetric, also called PKI, and Symmetric encryption.
The PKI uses public and a private key, and we use the keys to encrypt and decrypt the message, PKI is used where we have two different endpoints, so for example in integration scenarios like services integration or web browser accessing to a web server or a VPN network, SSH to transfer files or SFTP.
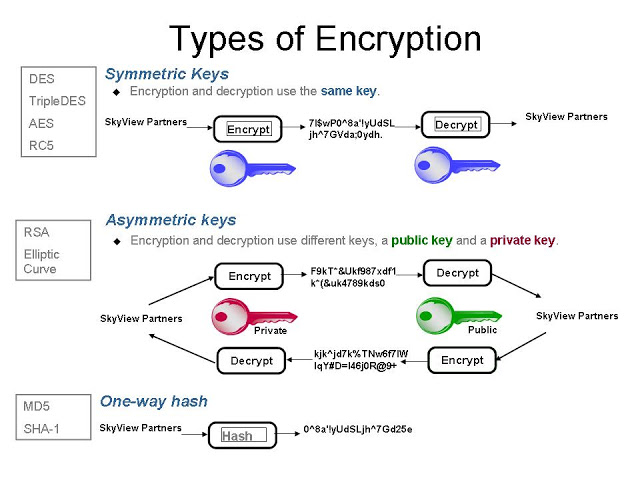
The Symmetric encryption is much faster than the PKI because it uses a single private key and for that reason, it is used where we need to encrypt data very fast, and we don’t have two endpoints.
The Symmetric encryption is used to encrypt data in a database, secure backup, security streaming, and any other similar scenario where data encryption is the point.
The symmetric encryption uses a different algorithm like DES, Twofish (Twofish, 2018) , 3 DES, Blowfish (Blowfish, 2018), the most used is the AES (Alfred J. Menezes, Paul C. van Oorschot and Scott A. Vanstone, 2001).
AES I very used because in the 2000 the National Institute of Standard and Technology (NIST) defined the AES as a common standard to use, after that the private sector started using it as standard as well, and this is another interesting case of collaboration between government and private sector (Alfred J. Menezes, Paul C. van Oorschot and Scott A. Vanstone, 2001).
It is important to use a standard protocol like AES because the cryptography community and companies test and invest more in a standard protocol that the others not standard, so we are confident that the protocol is more secure than the others.
AES is a block cypher because it works in blocks of 16 bytes if we need to encrypt 4 bytes than they are padded into 16 and encrypted and to enforce the AES encryption we can put in an initialization vector IV.
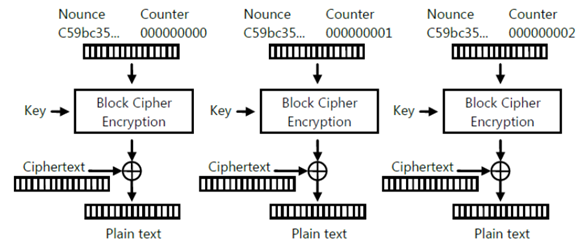
The most key size uses in AES are 128, 192 and 256 bit, larger is the key, and stronger is the encryption, but the performances decrease, and we need more resources to encrypt, for that reason it is important to generate a very strong key.
To generate a strong key we can use a technique like Cryptographic Secure Random Number Generator or Password-Based Encryption, many programming languages (.Net, Node.js, C++ and more) provide libraries for that (RandomNumberGenerator, 2018).
NIST provides certification as AES Test Validation to provide a standard certification to test the encryption software and to certify the correct use of AES by the software, very long and complicated path. (Cryptographic Algorithm Validation Program, 2018).
The hash algorithm is used for a completely different scope; it is used to check the integrity of the data, it is like a signature.
Hash algorithm has three main requirements, fast in the generation but secure; if you change a single byte of data then the hash must change completely, the third is the unicity of the hash, so it needs to be impossible to find the same hash for a different object signed.

About the hash collision the problem is not finding a document able to create the same hash in the world, this may be possible but very unlike, the problem is to avoid the possibility to generate the same hash, and this is what the bad guy tries to do, he may intercept, change it and send a fake document.
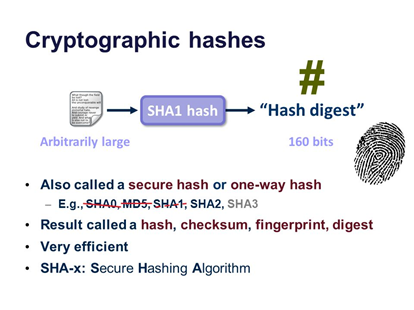
There are different types of the hash algorithm, MD5 was one of the most use but now easily breakable as SHA1, SHA2 is better but the standard and recommended is now SHA3.
References:
Twofish (2018) Available at https://www.schneier.com/academic/twofish/download.html (Accessed: 30/03/2018).
Blowfish (2018) Available https://sourceforge.net/projects/bcrypt/ (Accessed: 30/03/2018).
Alfred J. Menezes, Paul C. van Oorschot and Scott A. Vanstone (2001) Handbook of apply cryptography Available at http://cacr.uwaterloo.ca/hac/ (Accessed: 30/03/2018).
RandomNumberGenerator (2018) Available at https://msdn.microsoft.com/en-us/library/system.security.cryptography.randomnumbergenerator(v=vs.110).aspx (Accessed: 30/03/2018).
Cryptographic Algorithm Validation Program (2018) Available at https://csrc.nist.gov/projects/cryptographic-algorithm-validation-program/validation (Accessed: 30/03/2018).
‘Enhanced SHA-192 Algorithm with Larger Bit Difference’ 2013, 2013 International Conference On Communication Systems And Network Technologies, Communication Systems And Network Technologies (CSNT), 2013 International Conference On, Communication Systems And Network Technologies, International Conference On, p. 152, IEEE Xplore Digital Library, EBSCOhost, viewed 30 March 2018.

