This article assumes the reader has a basic understanding of Azure security and governance.
Many companies are exposing public IP and ports from Microsoft Azure, and many of them are unaware of that, a good practice is to check what we have open and why.
The port scanning of an Azure infrastructure can be very challenging, especially in global and enterprise scenarios where many Enterprise Agreements and subscriptions are involved. Luckily, we have some options to solve this problem:
- The first option is using PowerShell/Az CLI and create a script to list all ports opened by network security groups and firewalls, but I see a big problem with using this option. Companies and departments can decide different security firewalling strategies, it can be a network security group or Fortigate, for example.
- The second option can be using Azure APIs, which honestly is pretty powerful, and we work in JSON format for data that is very serializable and easy to manipulate, but also, in this case, we still have the same problem, we are not sure about what is protecting the IP exposing the port.
- The best solution is performing an active scan in all IP we find and using a proper tool like NMAP to do that, the reason for that is because I want to be sure about the ports open and I don’t want to depend by any API.
I consider NMAP one of the most powerful hacking tools which tons of options, not just scanning but also for advanced pentest operations, I recommend you to look at it.
Because of the complexity of a global Azure environment, the two main problems I see are about the reconnaissance and collecting all data I need and, second is the mapping between the IP and ports scanned and the Azure resource-related. Actually NMAP provides the possibility of scanning a list of IPs but how to map the hundreds of IPs provided by NMAP with the related Azure resources?
For that reason, I decided to integrate active hacking capabilities in Aziverso, which already has very powerful reconnaissance features and mix them together.
To access on any Azure resource, you need to set up an Azure service principal account or using an existing one, you can find all info in https://aziverso.com, and you associate the account to the scope area you want to scan, it can be a management group or multiple subscriptions.
If you like to scan the entire Azure Tenant you need to execute a privileged escalation to Global Admin and add the account to the Tenant Root Group
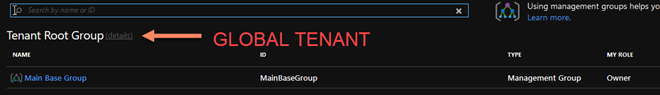
To obtain the full visibility you also need to escalate in the Azure AD Access management for Azure resources, set it to YES
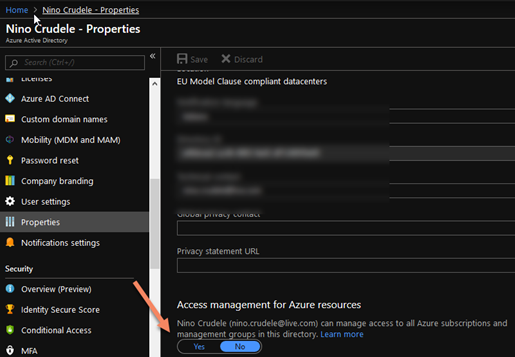
Log off and back again and you will see any Azure resource, subscription or management group associated with this tenant, they can be even related to other Enterprise Agreements and contracts, it doesn’t matter.
For privacy reasons, I am going to use my personal Azure environment, which actually contains five different subscriptions, I did the same operation with hundreds of subscriptions and different Azure EA without any issue.
First, I execute Excel, and from Aziverso Scaffold, I scan the tenant to retrieve the list of all subscription I see.
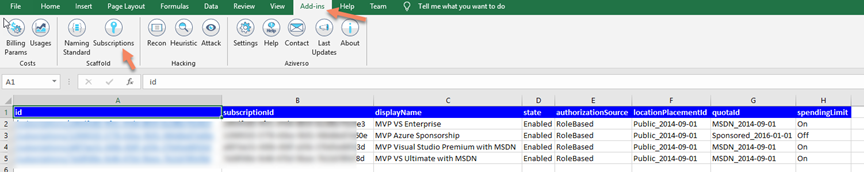
Now I have my surface attack, and it can also be a list of hundreds of subscriptions.
Now I use the Recon to retrieve all Public IP, the recon is a crazy amazing feature, it lists more than 2000 Azure APIs, and I can map the Excel sheets to map the values I want to pass to the API
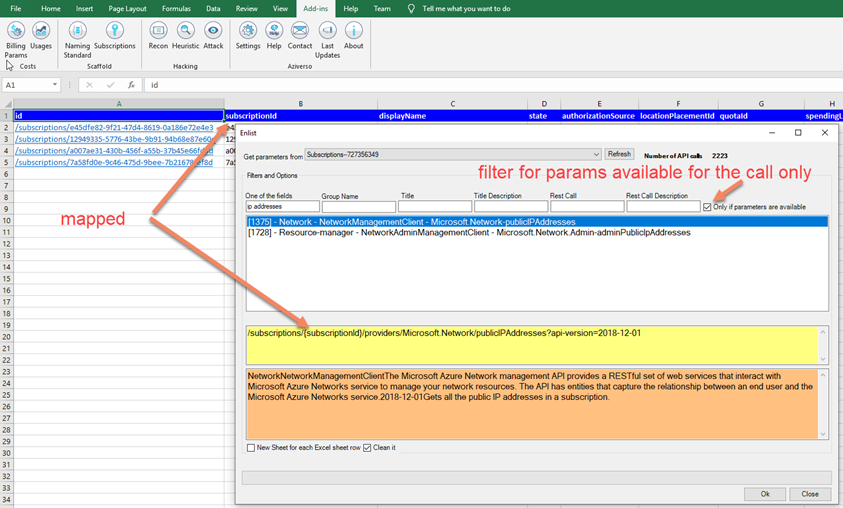
Now I have the list of all public IP
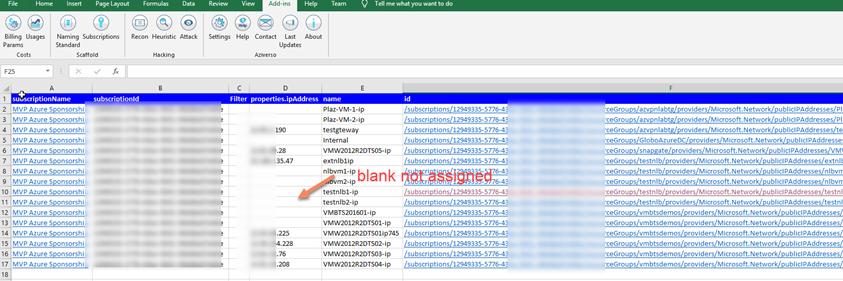
The blanks are not actually used of assigned so we can easily filter these using the Excel powerful filter and eliminate them from the list
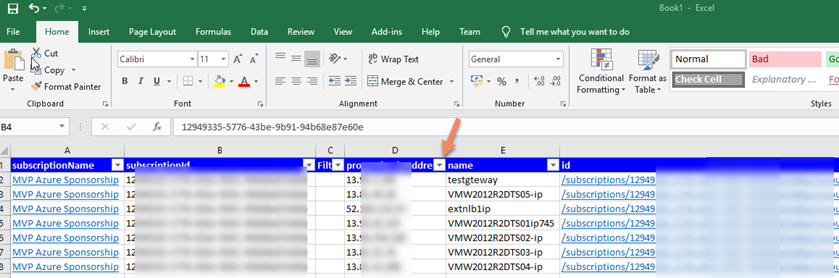
Now let do the magic, and it is time to scan!
In Aziverso I select Attack in the new Hacking area, and it will open the new feature
I select the type of attack I want to perform, in this case, an IP scan and it will use the powerful NMAP capabilities for that.
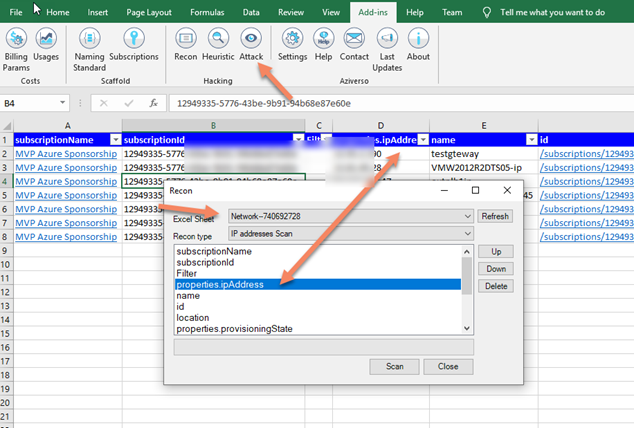
I clean up all parameters and press Scan (I am planning for a smart parameters mapping, no time for that now), go and take a good lunch + a coffee
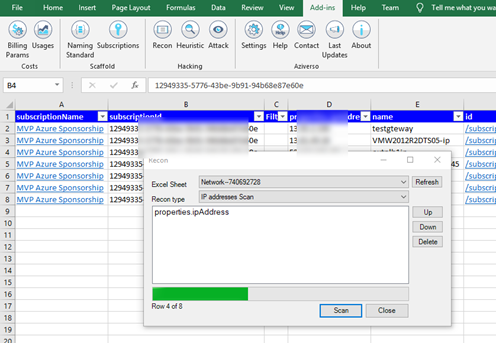
And here we have all the results!
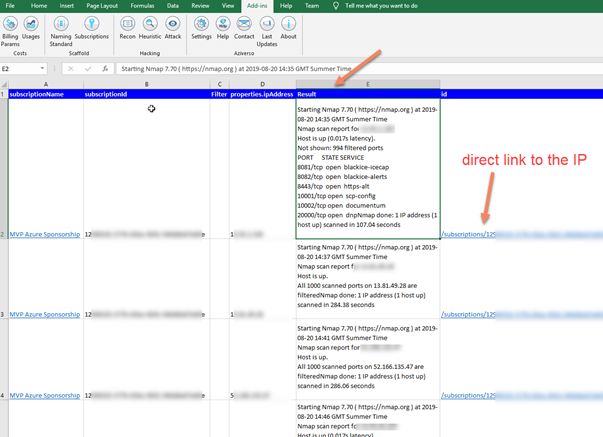
The great thing is also the possibility to have the link of the specific Azure resource scanned, and I can directly jump into the portal from Excel.
I am still working on this feature, and I will release in public very soon, feel free to contact me for any question and especially for collaboration, any kind of collaboration, code, design, hacking.
I have in plan many other hacking implementations like including advanced NMAP scans, Metasploit, Social-Engineer Toolkit, and with the inclusion of Windows Subsystem for Linux (WSL2), the pentest and hacking potentials are endless. For example, performing a scan on all the App Service endpoints in the entire tenant.
stay tuned! And ping me!

